Emsisoft Threat Hunting enables security analysts to proactively search for indicators of compromise (IOCs) across every endpoint. Use Threat Hunting to monitor endpoints for anomalous behavior, separate the usual from the unusual and intercept malicious activity.

Threat Hunting
Expose and neutralize threats lurking on the network with Emsisoft Threat Hunting, available exclusively in Emsisoft Enterprise Security.
THREAT HUNTING
Expose undetected threats
Unseen Threats
Absolute security doesn’t exist. There’s always a risk that a well-resourced threat actor is able to slip past an organization’s endpoint security measures undetected.
Silent Network Intrusions
After successfully penetrating the perimeter, a threat actor may remain hidden on the network for days, weeks or months, quietly studying the IT environment, harvesting login credentials and exfiltrating sensitive corporate data. Every moment that a threat remains undetected, the greater the damage potential.
Detecting Advanced Cyberattacks
Emsisoft Threat Hunting uncovers sophisticated cyberattacks and advanced persistent threats that may have evaded your initial endpoint security controls before more serious damage can be inflicted.
A 360-degree view of your environment
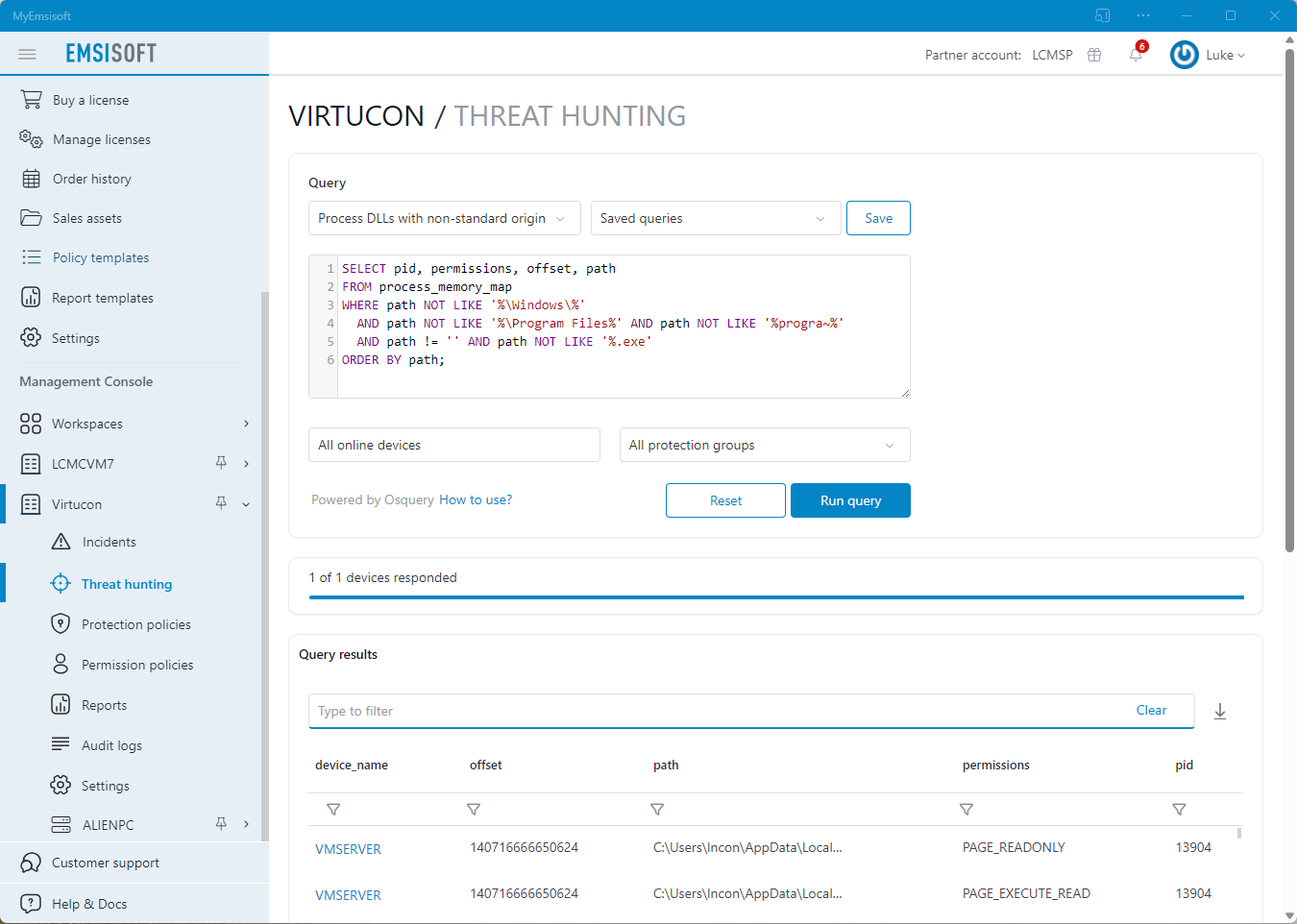
Save time with simple SQL queries
Simplify data aggregation. With Osquery, endpoints can be queried just like an SQL database, meaning organizations no longer need to run multiple system tools to get critical threat-related information.
Emsisoft Threat Hunting comes loaded with dozens of ready-to-use queries optimized for threat hunting. Use an off-the-shelf query or create custom queries tailored to the needs of your organization and save them for later use.
Check which networking ports are open and which processes opened them, filtering out regular web browsing activity.
See which programs and browser extensions are installed in Chrome, Firefox and Edge.
See what’s in your devices’ Downloads folders.
See which services are running.
Verify all user-installed and self-signed certificates.
Check the status of system features like BitLocker, Windows Defender Firewall and Security Center.
List all programs that start automatically at boot time.
Check which processes take up most memory.
See all scheduled tasks.
Check the DNS cache and the hosts file for suspicious hosts.
Check if any active processes have had their underlying EXE file on disk removed.
Get basic operating system information including build version, installed patches, uptime, etc.
Instant insight
All the information you need, all in one place. Whether security analysts are searching for evidence of emerging threats or carrying out a routine check to identify which systems contain vulnerable applications or drivers, Emsisoft Threat Hunting provides real-time visibility across all Emsisoft-protected devices. Results are displayed in a matter of seconds, making it easier and faster than ever to identify and eliminate threats lurking on the network.