Emsisoft releases new decryptor for STOP Djvu ransomware

While STOP (Djvu) may not be as well known as Ryuk and Sodinokibi, with 160 variants, more than 116,000 confirmed victims and an estimated total of 460,000 victims, it is by far the most active and widespread ransomware today. But there’s good news. We’ve just released a free decryption tool for it.
We’ll be breaking STOP’s encryption via a side-channel attack on the ransomware’s keystream. As far as we know, it’s the first time this method has been used to recover ransomware-encrypted files on such a large scale.
STOP is spread almost exclusively through key generators and cracks, which are tools that claim to enable people to activate paid software for free. Children and cash-strapped students commonly seek out these types of tools, which puts them at greater risk of encountering STOP and, by extension, their parents and anyone else who shares a device with them.
To make matters worse, some versions of STOP also bundle additional malware, such as password-stealing Trojans.
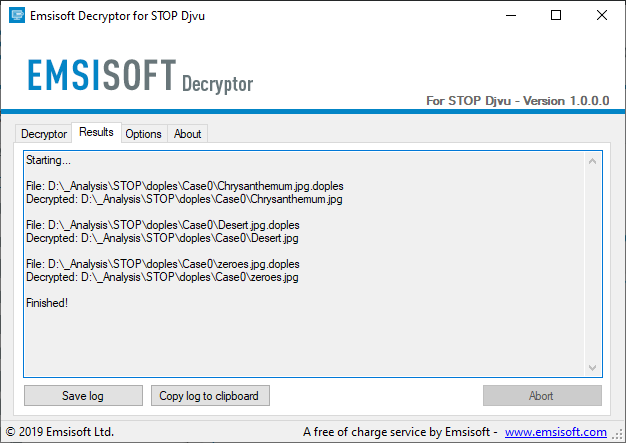
Our free decryption tool helps victims to unlock their files without paying the ransom, and can be downloaded from the Emsisoft Decryption Tools page linked below.
Unfortunately, this tool will not work for every victim as it can only recover files encrypted by 148 of the 160 variants. We estimate that this will enable approximately 70% of victims to recover their data. For people affected by the remaining 12 variants, no solution currently exists and we are unable to offer further assistance at this point in time. We recommend that those who find themselves in this position archive the encrypted data in case a solution becomes available in the future.
Download the STOP Djvu Decryptor here
Note: A decryptor for STOP Puma is also available here
STOP ransomware variants
The STOP ransomware family covers over 160 currently known versions, with four main variants. Each variant has differing levels of decryptability:
- UPPERCASE Variants (e.g. .DATAWAIT, .KEYPASS) – Some extensions of this variant can be decrypted by the STOP Puma decryptor by providing a single encrypted/original file pair over 150KB.
- Puma Variants (e.g. .puma, .pumas, .pumax) – All known extensions of this variant can be decrypted by the STOP Puma decryptor by providing a single encrypted/original file pair over 150KB.
- Old Djvu Variants (e.g. .djvu, .roland, .verasto) – The most prevalent variant. Encrypted files will always be 78 bytes larger than the original. All known extensions of this variant can be decrypted by the STOP Djvu decryptor (with caveats) in two ways: offline keys and several encrypted/original file pairs over 150KB.
- New Djvu Variants (e.g. .gero, .meds, .boot) – The latest variants of the STOP family started spreading in August 2019 and append various extensions to encrypted files, which are always 334 bytes larger than the originals. The STOP Djvu decryptor may work for these new variants, but only in limited circumstances.
Latest statistics
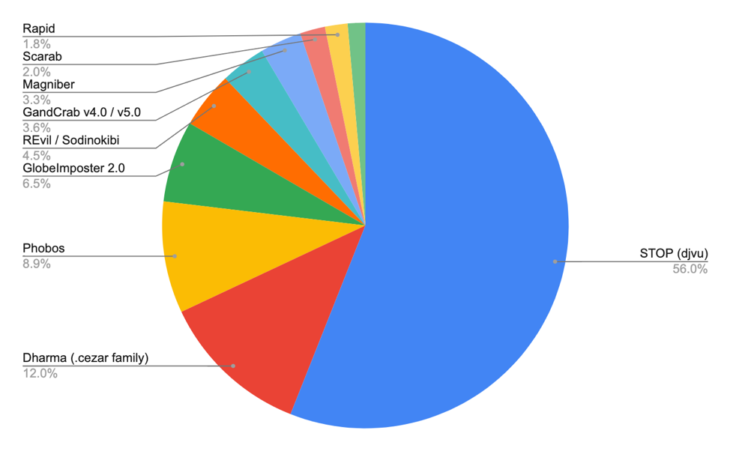
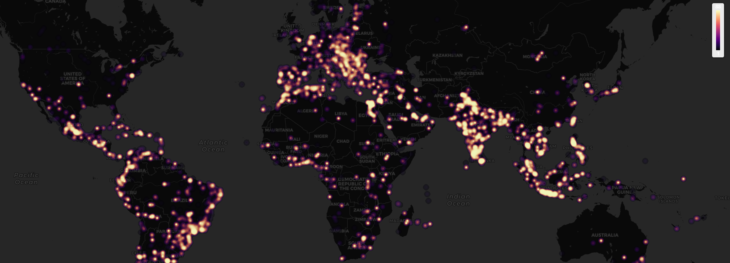
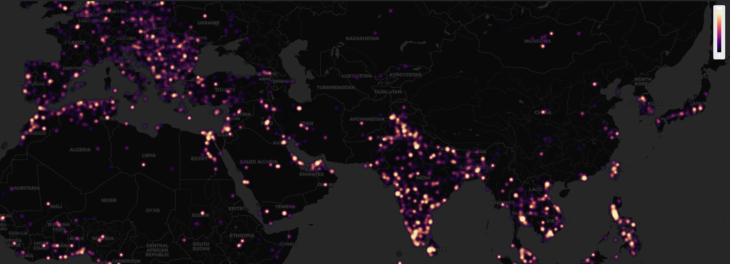
The data in our latest Ransomware Statistics report for Q2 and Q3 2019 shows that STOP accounts for more than half of all the ransomware submissions throughout the world.
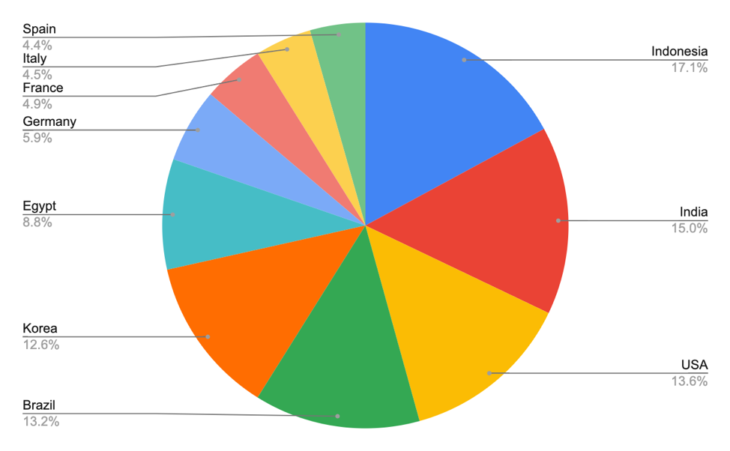
Indonesia, India and the USA top the list of the most ransomware submissions and account for almost half of all submissions. Incidentally, Indonesia has one of the highest rates of software piracy in the world.
The spread of STOP
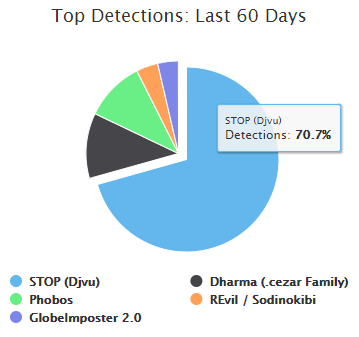
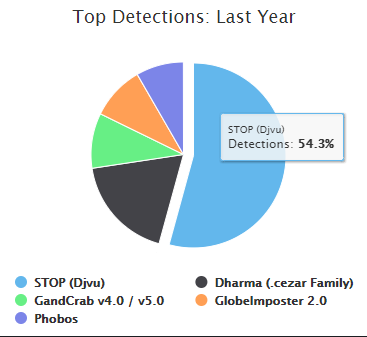
STOP has spread rapidly the past year. In October 2018, it took the top spot and accounted for 54.3 percent of the top five ransomware strains detected by ID Ransomware. By October 2019, it retains its top spot and now accounts for 70.7 percent of the top five detections in the past 60 days (from the time of publication of this post).
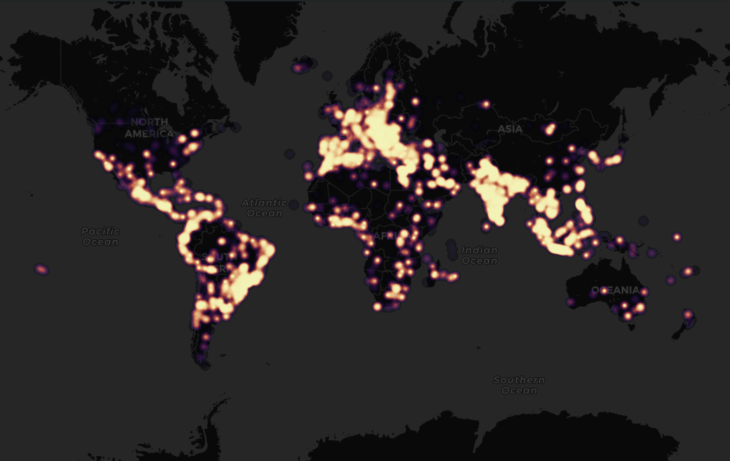
Detections throughout the globe
Technical details
STOP encrypts victim’s files with Salsa20, and appends one of dozens of extensions to filenames; for example, “.djvu”, “.rumba”, “.radman”, “.gero”, etc.
The ransom note “_readme.txt” contains the following text:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-sTWdbjk1AY
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
[email protected]
Reserve e-mail address to contact us:
[email protected]
Your personal ID:
[redacted]
Community collaboration
Efforts to help STOP victims have truly been a community collaboration! The good people at Bleeping Computer, for one, have helped numerous STOP victims by guiding them through the decryption process, supplying offline keys and samples and more.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialBecause of the very large number of people affected by STOP, we’re unable to provide one-on-one support for this tool. If you need help using the decryptor, please visit the STOP support topic at Bleeping Computer. The community members will be happy to provide assistance and we offer big, big thanks for their help.