The big ‘R’: Ransomware. Why businesses and institutions are at risk and what to do about it

Normally you would expect a ‘state of emergency’ at a hospital. And you’d expect to find cyber criminality somewhere else. But just imagine for a second: what, if the two met in the same place?
A hospital is a place where you’d go to seek advice, help, safety. Where you rely on the doctor’s knowledge and profession to make things better. But what if that place of shelter got in the center of a ‘cyber state of emergency’? No, we’re not trying to make up some scary stories. To give you a real life example, no embellished facts:
In February 2016 (just 3 months ago, that is), Hollywood Presbyterian Medical Centre was forced to declare an ‘internal state of emergency’ because of a ransomware held their files hostage. The incident left employees unable to access patient files and, in particular, emails. As a result, the hospital was unable to continue its day to day operations. Again, just imagine for a second: What, if Doctors could not access information about their patients anymore, their medical histories or the latest lab reports. No communication between other medical centers or medical staff was possible. In brief, it was a disaster.

According to an NBC news report, the Hospital paid a ransom of approximately US $17,000. Hospital CEO, Allen Stefanek, stated that paying the ransom of 40 bitcoins was “the quickest and most efficient way to restore our systems and administrative functions.” He said the hospital did it in the interest of restoring normal operations. In other words, their priority was saving lives.
To allow a better understanding of how this happened, let’s look at the timeline. The malware was initially noticed on the hospital computer on 5 February. It took another ten days for the hospital system to be restored to normal, after paying the ransom fee. For the third time in a row, just sit back and imagine, ‘what, if’ a hospital was unable to commence its daily business from one minute to the next – simply because of a ‘computer problem’. The Presbyterian Medical Centre in Hollywood was lucky – in the end – as fortunately, patient care was not affected, and there’s no evidence patient data was compromised, the hospital said in a statement.
Unfortunately, this story is just one of many. Smaller US Police Departments have also been affected, along with tens of thousands of home computers around the world on a daily basis. Most of the cases don’t even reach to the public surface as businesses want to avoid facing a loss of customers due to a lack of trust. Understandable, but it also plays into the hands of ransomware hackers who take advantage of the fear and silence their tactics create.
But, what exactly are we talking about?
Ransomware – a complex and difficult battlefield
In the ‘good old days’ of ransomware, a scam would simply lock the users’ screen and ask for a payment of $100 – $200 to unlock the screen. Simple. However, unlocking software solutions were often available and a ransom could be avoided. Nowadays, ransomware is infinitely more complex and difficult to decrypt. And here is why.
It is a ticking time bomb. Literally.
Modern ransomware often uses a countdown timer that puts pressure on the user / IT departments to pay the ransom within a short period, such as 48 hours. The victim has little time to search for a solution, which often results in them being forced to pay the ransom, or lose their data.
You cannot reach an attacker that lives in the cloud(s).
Modern ransomware often can’t be decrypted without paying the ransom. This is because all encryption info is stored on servers somewhere in the cloud which can’t be accessed in reasonable time – or at all. Cracking the password by brute force (this means to test all possible variants) is simply impossible as it uses strong encryption that cannot be cracked in a reasonable amount of time – even with the best supercomputer in the world.
Apparently, there is a perfect crime.
We can hear, read and fear as much as we want about the world being under constant surveillance. In this case, truly unfortunately, ‘Big Brother’ does not know everything. In fact, extortion payments via Bitcoin give attackers a method of payment that is impossible to trace.
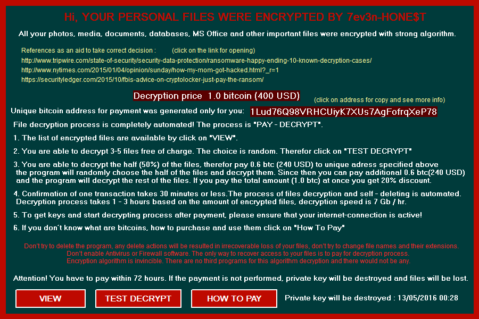
If you see this, you’ll need to act fast.
The perfect ransomware victims: Businesses
According to Security Magazine and the United States FBI, ransomware is on the rise in 2016. To hackers and cyber-criminals, it makes more sense to target businesses and institutions over home users.
Why are businesses such great targets?
- Blocking or theft of data from a business or institution can cost a business vast sums of money within a short timeframe.
- Businesses also have a reputation to lose – and word-of-mouth travels fast.
- Businesses not only have more to lose – they also have bigger funds than your neighbor next door.
- Last but not least, and the worst part of all: With the endless and trace-less paths of the World Wide Web, hackers use Bitcoin as a ransom payment, which makes the transaction virtually untraceable.

Ramsonware – a global threat to home & business users
What does ‘freedom’ from ransomware cost?
Sums vary widely, and it appears they range from smaller sums of $300 for home-users. Larger sums, such as the $17,000 paid by Hollywood Presbyterian Medical Centre above are being seen more often.
We have written many articles about ransomware and it’s ever-changing variations. Emsisoft first covered a story about ransomware in 2011 . We updated this with a further story about ransomware in 2013 along with dozens of posts about specific ransomware varieties on our blog. It is not only our conclusion that ransomware is continuing to become more complex, and more of a threat – unfortunately, it’s also the conclusion of many of the world’s leading news sources.
Enough scary words, let’s face life: What can YOU do to avoid a ransomware attack?
For starters, to avoid ransomware, it’s vital to update all computer software programs to their latest version. For example Adobe Reader or Skype. Do it right now. We mean it.
Then, installing high-quality, up-to-date anti-malware software, such as Emsisoft Anti-Malware or Emsisoft Internet Security will help detect unusual behavior and will often avoid an attack. Having said that, there is no software that can protect you 100% from ransomware, because of its’ nature.
How does Emsisoft help prevent ransomware on your computer?
Any ransomware that is being executed on an updated (again, do it right now!) system with Emsisoft Anti-Malware or Emsisoft Internet Security running, will be stopped before it can even begin to encrypt any user data. The Emsisoft behavior blocker is trained to detect any type of ransomware. As a demonstration, we recorded how Emsisoft responds to 20 well-known ransomware examples.
What to do if you’ve been attacked by ransomware
Our research team, in particular, Fabian Wosar, develops decrypters for new versions ransomware that has just emerged. We suggest you bookmark this page to get the latest ransomware decrypters from Emsisoft.
Further help and support can be found with our respected friends and at Bleeping Computer, where Emsisoft’s ransomware decrypters are often featured.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialAt Emsisoft we care about you, your business and possible threats. Immediately, no questions asked. If you get in trouble – get in touch!


