Ransomware incidents should be treated as data breaches and immediately disclosed

Over the course of 2020, we’ve seen a sharp increase in the use of data-stealing ransomware, an innovative breed of ransomware that not only encrypts a victim’s data, but also extracts it to the attacker’s server.
The stolen data is primarily used as leverage to encourage victims to pay the ransom. However, there is clear evidence indicating that cybercriminals are also using the data to carry out spear phishing attacks on business partners and customers of the victim company.
We strongly recommend that organizations come forward about ransomware incidents as quickly as possible. Disclosing incidents, particularly those involving ransomware that is known to be capable of data exfiltration, is critical in order to help other companies avoid becoming the next victims.
“Information is power and, in cybersecurity, it’s the power to prevent other similar events.” — Marc Barrachin and Algirde Pipikaite
A lack of disclosure
As it stands, there’s no legal requirement for companies to disclose a ransomware incident. Affected organizations can simply resolve the issue – which may or may not involve paying the threat actors – and resume normal operations, without informing their customers, partners or the general public of the incident.
With conventional ransomware, this is a somewhat understandable response. Yes, the company’s data has been encrypted, but it hasn’t been read, manipulated or extracted. Theoretically, no personally identifiable information (PII) has been exposed, so why should the company burden itself with the reputational loss and business interruption that inevitably come with disclosing a ransomware incident?
This argument doesn’t hold up when it comes to data-stealing ransomware. Many ransomware groups – including Maze, DoppelPaymer Sodinokibi and Nemty – have begun using techniques that enable them to extract a victim’s data to a remote server, where it can be processed, read and used however they deem fit. The stolen data is typically used as leverage to incentivize ransom payments, but we now have reason to believe it is also being used to carry out spearphishing attacks.
Data theft fuels spear phishing
Spear phishing is a highly targeted attack in which cybercriminals target specific individuals in specific organizations to gain access to important information such as financial data, staff credentials or, in this case, to deliver ransomware via malicious email attachments.
The fact that the actors have access to one company’s data – and, in some instances, emails – enables them to create extremely convincing email messages. In some cases, those emails may even take the form of a reply to an existing message, which means the recipient may be far less likely to question its legitimacy.
Companies standing silent to protect their reputation
When a company is hit with ransomware, its customers, suppliers and business partners should be on high alert for targeted attacks. Unfortunately, this usually isn’t the case. Given that there’s no legal requirement to disclose ransomware incidents (unlike data breaches, which must be disclosed) there’s little motivation for companies to come forward and admit they’ve been hit with ransomware.
Figures from ID Ransomware, a free tool that victims can use to identify ransomware strains, indicate that many organizations are more willing to pay hackers than compromise their reputation by admitting an incident.
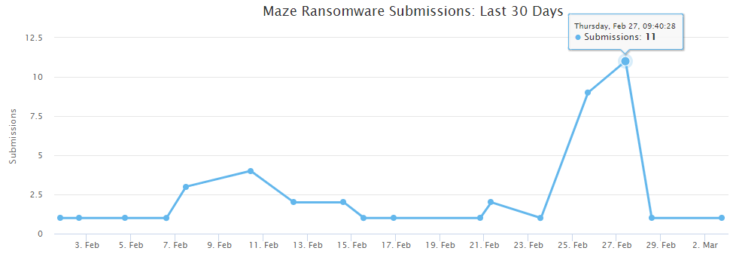
ID Ransomware shows that there have been 42 Maze submissions in the last 30 days. Given that only about 25 percent of victims upload to ID Ransomware, the real number of Maze incidents is probably about 168. However, the Maze website lists just 32 ransomware-affected companies that have refused to pay the ransom, only 8 of which were added within the last 30 days.
Why the discrepancy? Given that Maze only names those companies that don’t pay the ransom, the most likely explanation is that other companies paid the ransom to avoid being named.
Our recommendations
As data-stealing ransomware continues to become more common, it’s time to start calling ransomware incidents what they really are: data breaches.
All ransomware events should be considered data breaches until proven otherwise. Ideally, governments should legislate that ransomware incidents be treated as breaches and require affected organizations to issue notifications immediately.
Absent such legislation, we call on companies to make prompt voluntary disclosures of all ransomware incidents. While companies may prefer to delay disclosing in order to assess the legal implications of a breach and devise their crisis communication strategies, they should be aware that doing so could put their business partners and customers at significant risk.