When a surveillance state hacking firm gets hacked

This past Sunday, a Milan-based surveillance company by the name of Hacking Team got a taste of its own medicine. A 400 GB torrent file of internal documents, communications, and code was uploaded to the internet by an unknown hacktivist.
An embarrassment to surveillance states everywhere
Hacking Team is a surveillance firm used by government agencies around the world, including (but not limited to) organizations from Russia, Ethiopia, Saudi Arabia, Mexico, Hungary, Spain, and the United States. With all the information that has been released on its scores of clients, Hacking Team is urging its customers to stop using its software, and has yet to regain control over its email system.
If the hack itself isn’t enough to inspire doubt in big surveillance states, some of the compromised information might: leaked client passwords include such embarrassments as, HTPassw0rd, Pas$w0rd, and Passw0rd.
A security engineer’s worst nightmare
Hacking Team’s security engineer, Christian Pozzi, had his password store exposed, which revealed even more simple and straight-forward passwords to the company’s social media, financial, and network accounts. The word “kittens” was Pozzi’s personal administrative password.
If there were ever a reason to question government agencies and their surveillance aptitude, it’s this entertaining security fiasco.
The biggest and most influential governments of the world have hired a company that fails to enforce the basic principles of password creation. More importantly, this is a company that governments choose to entrust with highly sensitive information.
Naturally, Pozzi is claiming the leaked file has malware and has threatened unidentified hackers with incarceration and legal action. His twitter was subsequently hacked and has since been deleted, but you can see an archive of the social media account here.
Into the dark abyss
One of the most interesting aspects of this incident is that it allows an in-depth view into how companies like Hacking Team operate. And the view most definitely isn’t pretty… Hacking Team, just like many government agencies, have been secretly collecting exploits within software products in order to compromise systems. Without requiring any user interaction at all.
It comes as no surprise that these vulnerabilities have been adapted by various popular exploit kits within hours of the leak and are now used by cyber criminals to target millions of unprotected users. Also, routines were found within the Hacking Team command and control panel, that seem to allow anyone to place discriminating evidence like child pornography or bomb construction manuals on a compromised system:
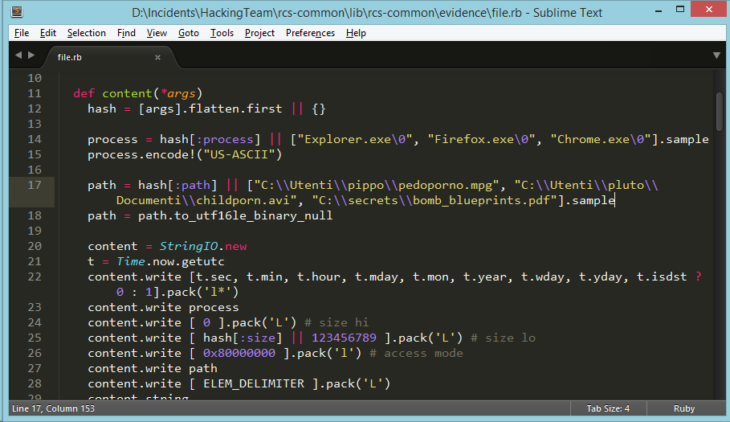
How Hacking Team operates definitely isn’t pretty.
This fuels many state malware opponent’s concerns, that malware that is used by government agencies for surveillance and evidence collection can easily be used to place the very same discriminating evidence. Therefore, any evidence collected through such means is not trustworthy by default.
The beginning of the end for Hacking Team
Regardless of what the Hacking Team does from here on out, the damage has been done—not only has a good amount of internal and customer information been compromised (clients as big as The Army of South Korea and The Federal Bureau of Investigation of the United States), but it may be facing serious legal trouble: Hacking Team claimed to have never done business with Sudan, and yet the released information shows otherwise. This potential partnership could be in conflict with the UN’s arms embargo on Sudan, which includes a prohibition on “technical assistance.”
While this story is still developing, it might interest you to learn more about Hacking Team on the Reporters Without Borders Enemies of the Internet index. You can also view a curated slideshow of the hacked material here, curtesy of CSO Online.
How does it affect me?
The Internet, and therefor hackers as well as government agencies, can only surveil, store and analyze what they are fed via different sources. It is out of the question, that using malware to get access to any kind of private communication or company secrets is faul play. Usually, it is just a matter of time until government supported malware projects tend to be discovered and shared with the public just as well.
The use of strong passwords, encrypted communication and trustworthy security software is your first level of defense. It should go hand in hand with updating your operating system, cleaning out your mail account (e.g. move old mails to a local backup instead of storing all of it permanently online) and changing your passwords on a regular basis.
Whatever you choose to share with the world by using Internet technology, remains for the most part, up to you. With that in mind, you are the warden of your own privacy.
Have a great, surveillance-free day!