Chinese hacker group APT use Microsoft’s Technet web portal to obfuscate their CnC servers

 Hackers and malware writers are now using the legitimate functions of popular websites to obfuscate or hide their malicious operations. In a recent attack on Technet, Microsoft’s blog for IT professionals, a Chinese hacker group APT17 used the ability to create profiles and posts to embed encoded CnC (Command and Control) to be used with a variant of the malware known as BlackCoffee. This was done to make it difficult for security professionals to trace the actual location on the CnC server, thus allowing it to remain hidden and operational. According to FireEye, several hacking groups are using the same obfuscation tactics on legitimate websites in order to prolong the lifetime of their CnC servers and thus spread more malware.
Hackers and malware writers are now using the legitimate functions of popular websites to obfuscate or hide their malicious operations. In a recent attack on Technet, Microsoft’s blog for IT professionals, a Chinese hacker group APT17 used the ability to create profiles and posts to embed encoded CnC (Command and Control) to be used with a variant of the malware known as BlackCoffee. This was done to make it difficult for security professionals to trace the actual location on the CnC server, thus allowing it to remain hidden and operational. According to FireEye, several hacking groups are using the same obfuscation tactics on legitimate websites in order to prolong the lifetime of their CnC servers and thus spread more malware.
Hacker group based in China using notorious “BlackCoffee” malware
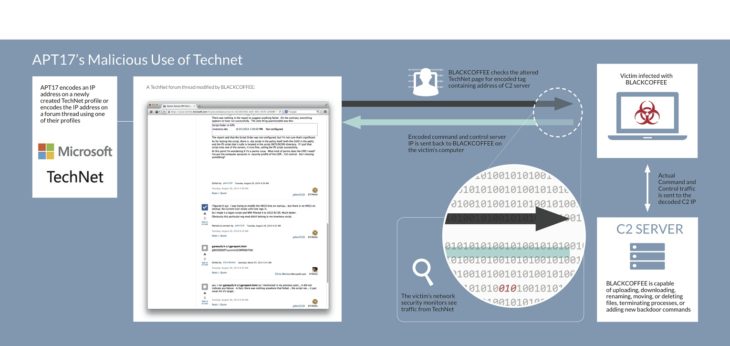
The culprits in this case, China-based hacker group APT17 (also known as DeputyDog) are notorious for their network intrusions against U.S. government entities, the defense industry, law firms, information technology companies, mining companies, and non-government organizations. The malware used, BlackCoffee is capable of uploading and downloading files; creating a reverse shell; enumerating files and processes; renaming, moving, and deleting files; terminating processes; and expanding its functionality by adding new backdoor commands. In short, a pretty troubling set of malicious operations. This malware, prevalent since 2013, is orchestrated by CnC servers. The communications between the infected system and the CnC server are carried out, disguised as search engine queries.
The BlackCoffee malware works by linking to the biography section of a profile or forum thread created by the attacker. As stated in this report by FireEye:
This BLACKCOFFEE variant contains one or more URLs that link to the biography sections of attacker-created profiles as well as forum threads that contain comments from those same profiles. A URL is randomly selected and the malware searches at that location for an encoded IP address located between two tags, “@MICR0S0FT” and “C0RP0RATI0N”.
This illustration shows how APT17 managed to maliciously use Technet:
New challenges for security researchers
In this case, the issue was resolved by encoding a sinkhole IP addresss into the profile pages and forum threads. The deviously created profiles were also identified and locked to prevent the attackers from making any changes. Microsoft have updated the signatures of their security products and FireEye have released Indicators of Compromise (IOCs) for BlackCoffee. A collaborative approach was helpful in identifying this threat, and its victims. As hackers develop new techniques, security experts must also be prepared to meet new challenges.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialHave a nice (malware-free) day!