Emsisoft releases a free decrypter for the GetCrypt Ransomware

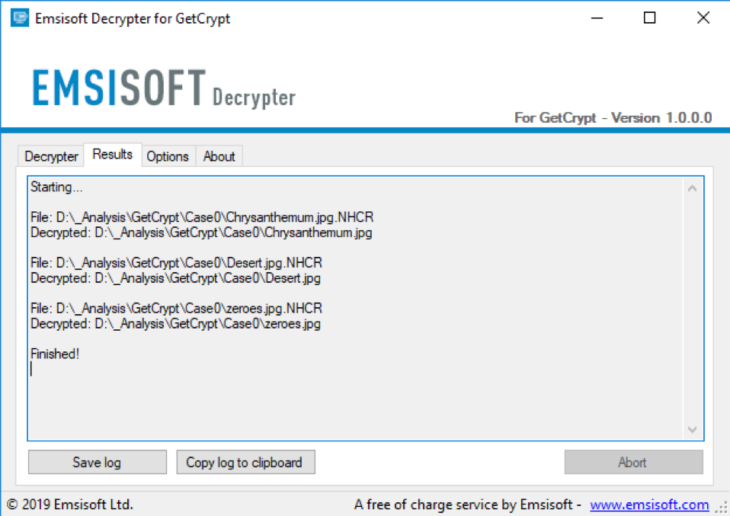
Our malware team just released a decrypter for the GetCrypt ransomware.
GetCrypt is a ransomware spread by the RIG exploit kit and encrypts files using Salsa20 and RSA-4096. It appends a random 4-character extension to files that is unique to the victim such as four random uppercase letters (e.g. .NHCR) generated from the victim’s CPU’s serial number. A test version used a static “.EZDZ” extension.
According to BleepingComputer‘s Lawrence Abrams, GetCrypt will utilize the WNewEnumResourceW function to enumerate a list of available network shares, or if it fails, will try to brute force network account credentials instead.
Malware researcher @nao_sec discovered the ransomware and ethical hacker @VK_Intel shared his analysis of the exploit to BleepingComputer.
If you’re a victim of this ransomware, DO NOT PAY the ransom. Download the decrypter and reach out to us if you have any questions.
Technical details
The ransom note “# DECRYPT MY FILES #.txt” contains the following text:
Attention! Your computer has been attacked by virus-encoder!
All your files are now encrypted using cryptographycalli strong aslgorithm.
Without the original key recovery is impossible.
TO GET YOUR DECODER AND THE ORIGINAL KEY TO DECRYPT YOUR FILES YOU NEED TO EMAIL US AT: [email protected] It is in your interest to respond as soon as possible to ensure the restoration of your files. P.S only in case you do not recive a response from the first email address within 48 hours,
[redacted]Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free Trial