Emsisoft releases a free decrypter for JSWorm 2.0 Ransomware

Our malware research team just released a decrypter for the new ransomware we nicknamed JSWorm 2.0.
Update: The JSWorm 2.0 decrypter has been updated for the extension ‘.JURASIK’
JSWorm 2.0 is written in C++ and uses Blowfish encryption. We call it “2.0” because there was another C# ransomware that used the “.JSWORM” extension. Some strings also suggest this ransomware may be from the same author.
Notable callouts were also found in two different malware samples naming ID Ransomware and several prominent malware researchers:
“:HI SIRI, DEMONSLAY AND AMIIIIGO!!! HOW ARE YOU?”
and
“:ID-RANSOMWARE, IT’S JUST THE BEGINING [sic] OF SOMETHING NEW…”
There have been multiple confirmed submissions to ID Ransomware (a website where victims upload their encrypted files to identify the ransomware that has encrypted their data) since January 2019, including victims from South Africa, Italy, France, Iran, Vietnam, Argentina, United States, and other countries.
Its files have the “.[ID-<numbers>][<email>].JSWORM” extension and the ransom note file named “JSWORM-DECRYPT.txt.”
If you’re a victim of this ransomware, please follow the instructions below and DO NOT PAY the ransom
Technical details
A JSWorm 2.0 infection will also have the following effects:
- Sets the “EnableLinkedConnections” registry key, which allows it to attack mapped drives when ran as admin.
- Restarts SMB services (lanmanworkstation) to take effect (we are investigating if there’s more to the SMB vector).
- Stops services for databases (MSSQL, MySQL, QuickBooks), kills shadow copies, disables recovery mode.
The ransom note contains the following text:
All your files were encrypted!
Your personal ID: [redacted]>>> Contacts:
[email protected]
[email protected] (in case of no answer)>>> What should I include in my message?
1. Country
2. List of encrypted drives and their size
3. Extension of encrypted files (.[ID-[redacted]][[email protected]].JSWORM)
4. JSWORM PUBLIC KEY (below)>>> Free decryption as guarantee!
Before paying you send us up to 3 files for free decryption.
We recommeded to send pictures, text files, sheets, etc. (files no more than 1mb)>>> ATTENTION!
1. Do not rename encrypted files.
2. Do not try to decrypt your data using third party software, it may cause permanent data loss.
3. Decryption of your files with the help of third parties may cause increased price (they add their fee to
our) or you can become a victim of a scam.——-BEGIN JSWORM PUBLIC KEY——-
[redacted]
——-END JSWORM PUBLIC KEY——-
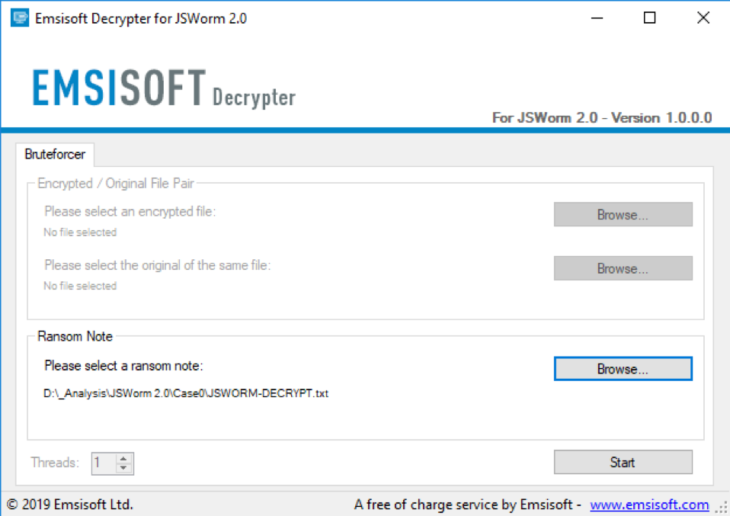
To use the decrypter, you will need the ransom note.
How to use the Emsisoft JSWorm 2.0 Decrypter
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trial- Download the Emsisoft JSWorm 2.0 Decrypter.
- Run the executable and confirm the license agreement when asked.
- Click “Browse” and select the ransom note file on your computer.
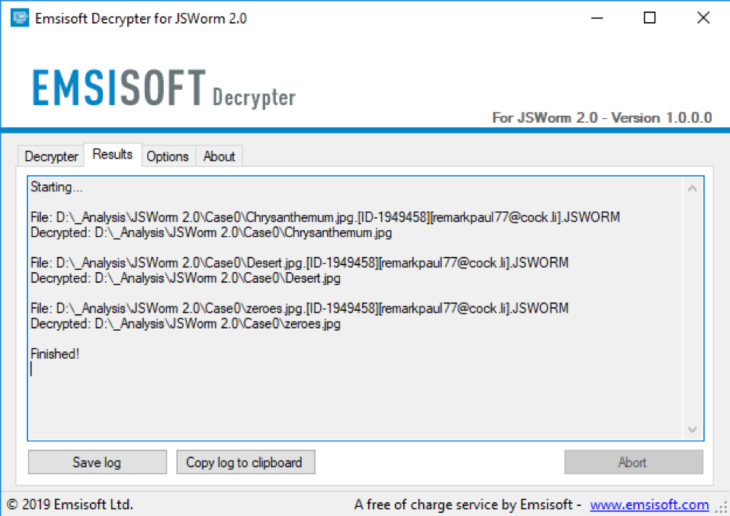
- Click “Start” to decrypt your files. Note that this may take a while.
Finished!