Security Essentials. NOT !
Rogue Security products are constantly submitted to us by our customers and researchers for analysis, and carrying on our little analysis report of something interesting we come across while doing those analyses. This week our research lab got to meet a rogue product faking itself to be Microsoft’s security product, Microsoft Security Essentials. Let us see what we found.
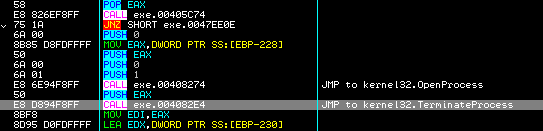
Every rogue variant tries to do something different to fool end users or make job of virus researchers a bit harder. When we started analyzing this variant, we saw that when this rogue is active in a victim’s system, the malware will monitor every process. At the instance when an application is executed the rogue will terminate the process responsible.
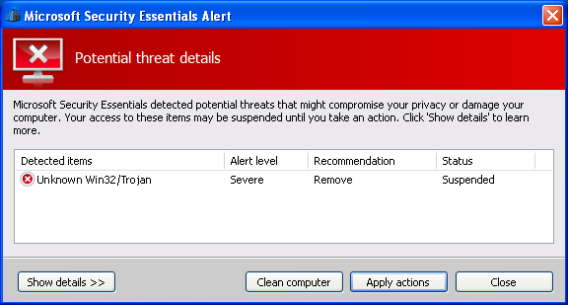
And then shows the following fake alert
The rogue has a hard coded list executables which will be blocked.
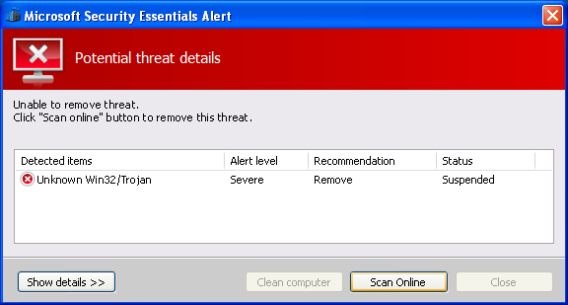
With the Alert prompt on the face, if the user clicks “Clean Computer” or “Apply actions”, the application says “Unable to remove the threat”.
Running out of options, the user moves on to “Scan Online”, when he is redirected to the address below
– http://abcd799d2aae82bad9effd7a716d2.co.cc/pipec/new.php?id=allinone
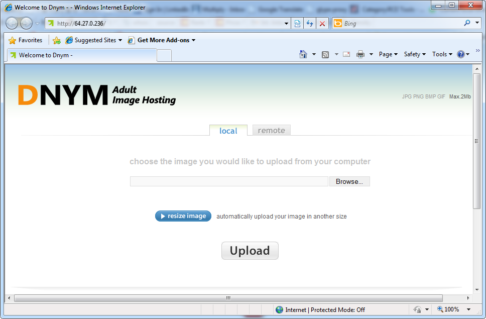
And displays the screen
The images including the antivirus logos navigate to
– http://64.27.0.236/images/pb.gif
– http://64.27.0.236/images/pca.png
– http://64.27.0.236/images/pb.gif
– http://64.27.0.236/images/NOD32.gif
– http://64.27.0.236/images/IKARUS.gif
– http://64.27.0.236/images/VirusBuster.gif
– http://64.27.0.236/images/VirusBuster.gif
which ofcourse when the aforesaid IP is visited, we are presented the website below
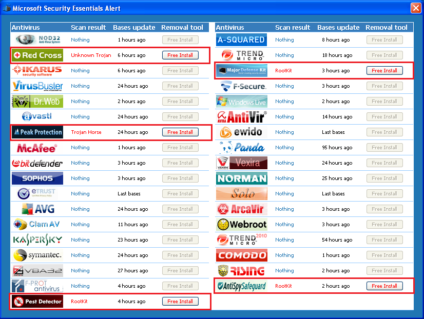
The social engineering attempts by these malware authors are never-ending but as always have more than one loophole. And if we give a close look at the Alert window with multiple AV vendor recommendations, we will see all “legitimate” vendors have scan result as “nothing” and removal tool button is disabled. The ones with enabled links are Red Cross, Peak Protection, Pest Detector, Major Defense Kit and AntiSpySafeguard. Let’s look into some of these.
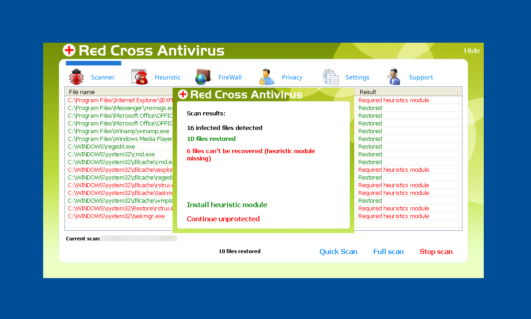
Red Cross
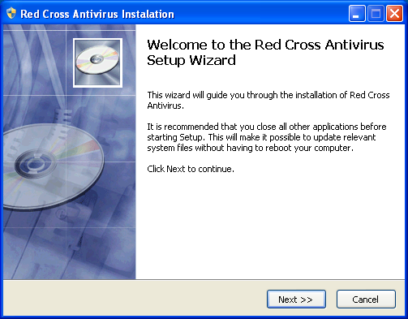
When an user chooses and clicks Red Cross enabled removal tool, the user is navigated to http://abcd799d2aae82bad9effd7a716d2.co.cc/pipec/setup_rca.exe and the rogue variant is downloaded.
During the installation process, the rogue connects to the address http://abcd799d2aae82bad9effd7a716d2.co.cc /inst.php?id=hiro01
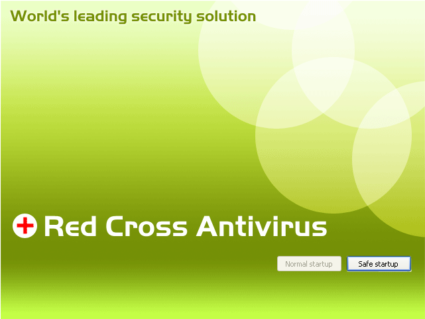
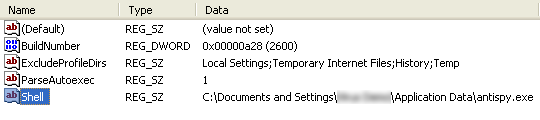
The system restarts after the installation, and the user is presented a desktop with a screen like below but no start button, taskbar nor desktop icons.
We found out the rogue had changed the shell from explorer.exe to the malware executable.
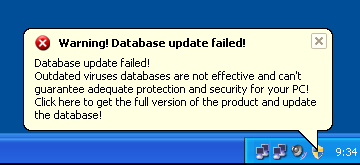
Fake Alerts do continue
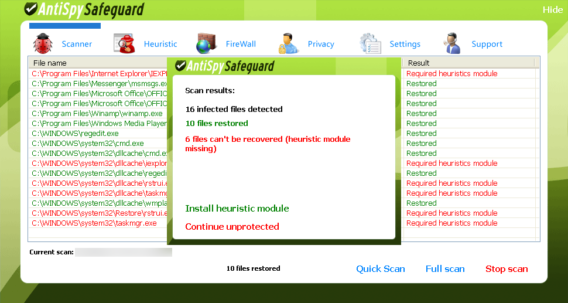
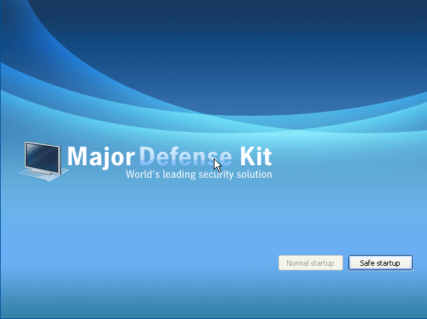
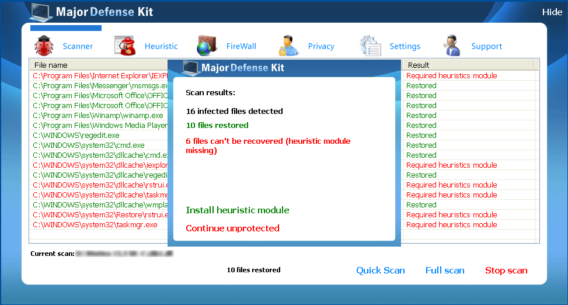
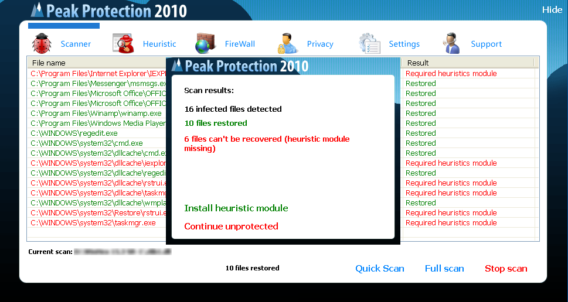
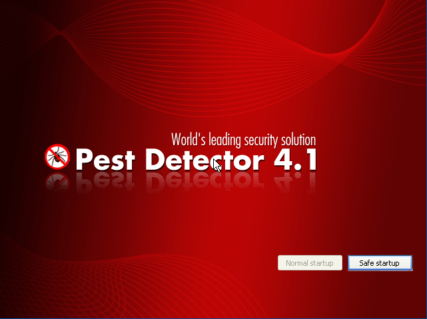
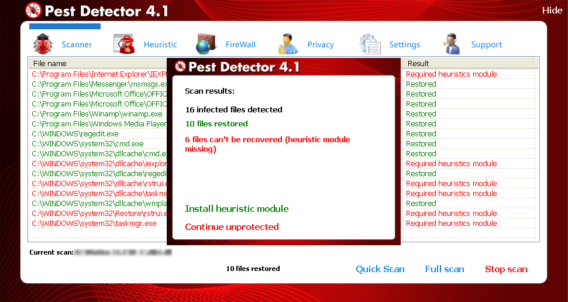
We did further analysis on Peak Protection 2010, Pest Detector, Major Defense Kit and AntiSpySafeguard which showed similar behaviors of Desktop background screen and fake warnings. Some screenshots of such behaviors are given below for further awareness.