Protector Rogue Re-emerges
As recently discussed in our post about Hacking Identity Theft, there are number of ways that malware can work its way onto your computer. One of the most common modes of entry is through a Trojan Horse program that fools you into installation by presenting itself as a useful plug-in or application.
 Rogue security software is a type of Trojan that presents itself as antivirus software, and right now there is a very pesky type of rogue circulating the Internet that is very similar to what was called The Protector Rogue, in 2012.
Rogue security software is a type of Trojan that presents itself as antivirus software, and right now there is a very pesky type of rogue circulating the Internet that is very similar to what was called The Protector Rogue, in 2012.
The Protector Rogue took its namesake from the file-name protector-xxx.exe (where x’s were random letters). This malware was very common until it was for the most part eradicated in September of last year. This new version of the Protector Rogue has the file-name guard-xxx.exe and the registry run value GuardSoftware.
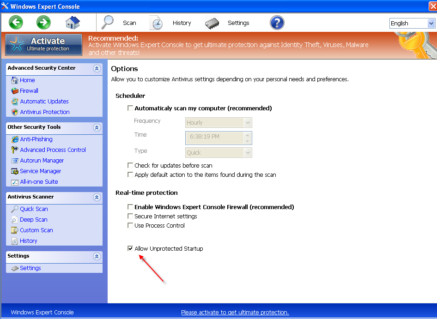
Because hackers are generally lazy, they usually base new malware of off older versions, and GuardSoftware has many of the same components that Protector did. In fact, despite the name change, even the Graphical User Interface (GUI) is still setup for Windows XP.
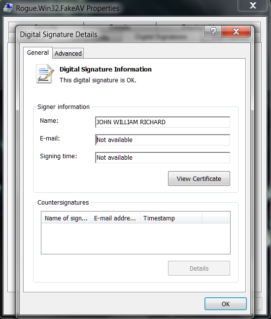
This unchanged GUI is a dead giveaway to anyone running anything past XP. The makers of GuardSoftware have implemented a few new tricks, however, and it’s for this reason that the malware is starting to work. GuardSoftware’s installer, or dropper, has a valid digital signature, which makes it more trustworthy to the human eye at glance and which will bypass certain forms of heuristic detection.
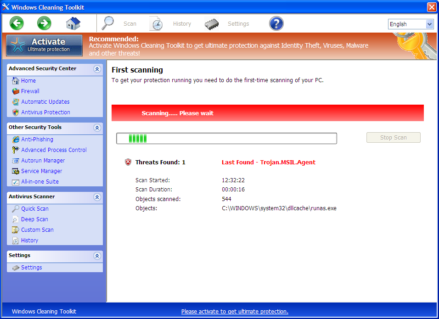
At the same time, GuardSoftware utilizes hijacking techniques not previously observed in comparable rogue programs. After installation, GuardSoftware restarts your computer and then essentially locks your desktop with a “Scanning In Progress” screen.
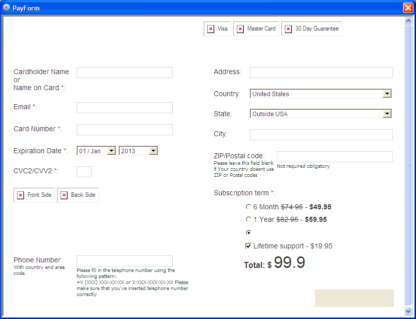
This screen is meant to fool users into trusting GuardSoftware, and it even goes as far as allowing you to “disable” the scan through an “Options” feature. This faux-disable will unlock your desktop, but it will not stop the scan. Instead, the supposed scan will continue to run in the background, with constant pop-up reminders that your computer is infected, all aimed at persuading you to purchase the full version of GuardSoftware, by entering your credit card information into a screen like this:
GuardSoftware is one of the first rogue programs to utilize such screen locking, which in the past has typically only been observed in ransomware. In the past, Protector Rogues would instead just scare users with frightening messages, such as YOUR COMPUTER IS INFECTED or PROTECTOR FOUND 136 VIRUSES ON YOUR COMPUTER!!! It would seem that whoever developed GuardSoftware has realized that most computer users are no longer so gullible, and that a more forceful approach is necessary.
This rogue family uses a variety of names, some examples are Windows Expert Console, Windows Cleaning Toolkit and Windows Active Hotspot. Below are some sha1 hashes listed for these variants:
- FAAB416D4423F08337707D6FC15FA4ACA143D9BE
- 2966D9B0B7B27C1CA2FA46F93E26E82FBB7FE64C
- CB8B40EACC05C5D34396D70C9B9C1D931A780517
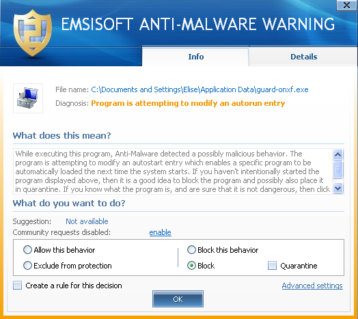
Fortunately, anyone running the full version of Emsisoft Anti-Malware is protected from the GuardSoftware rogue. Emsisoft Anti-Malware features a Behavior Blocker which is designed to recognize rogue behavior where the human eye and other antimalware programs that rely on heuristic detection cannot. Emsisoft users who come across GuardSoftware can expect a prompt warning from a screen like this:
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialOur recommendation is to block the program immediately and to identify exactly where GuardSoftware was encountered so that the point of contact can be avoided and that you can warn your friends. In the meantime, we here at Emsisoft will continue to monitor GuardSoftware as it inevitably evolves and develops. If it is anything like its predecessor, it will be around for some time…but it will also eventually be defeated ;)