Phishing emails defraud thousands of users every day


Have you ever been surprised to receive an email from a well known company like DHL, Amazon or a particular financial institution from time to time? If not, you should be, especially if you have never done business with them before. Often, these emails are not sent by the aforementioned corporations, but instead by criminal scammers. In this article we will share some current examples of phishing emails and explain how to recognize them and protect yourself against them.
How phishing works
Scammers favor using well-known company names for two reasons; first, these names appear trustworthy and second, the odds are quite high that the recipient is an actual customer of theirs. The objectives of these fake emails vary; from “only” attempting to spy on the recipient by collecting data, to trying to infect your PC with malware or even defraud you of your money using various methods.
Example 1:
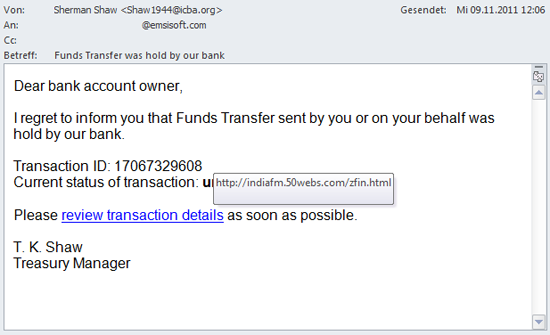
This is a classic phishing attempt, though fortunately a very bad one. What is most striking is the poor grammar and the absence of the company’s return address. Not only is it unclear which company Mr. Shaw even works for, but the dubious email address should also leave you suspicious.
You may also have noticed that the email doesn’t address you personally. Now let’s take a closer look at the link we are invited to click on. The screen shot clearly shows a suspicious URL hidden behind the link. You just need to hover your mouse over the link to see the resulting address. If despite these warning signs you nevertheless click on the link, you will be asked to enter your credit card details on a questionable looking website. If you proceed to enter your data then you can expect to discover unauthorized transactions on your next credit card bill.
Example 2:
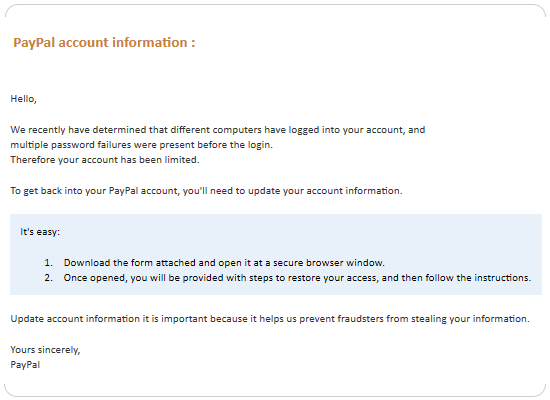
This is a slightly better attempt and is aimed at recipients using the online payment service PayPal. They claim that there were failed login attempts and the recipient should therefore open the file attached to the email. The recipient will then be asked to enter their account details and if they do, the scammer gains full access to their Paypal account.
As customers usually have a positive PayPal balance or at least have their bank or credit card details saved within PayPal, the goal is obvious – the victim’s money will quickly be transferred to other Paypal accounts and thus into the criminal’s pockets. Furthermore, opening the attachment is also likely to infect the victim’s PC with malware.
Again, the fact that the email isn’t personally addressed to the customer stands out. Official emails from PayPal always start by personally addressing you. In addition, neither PayPal nor any other company will send you emails asking you to enter your login data, or open attachments, with the exception of PDF files in rare cases.
Example 3:
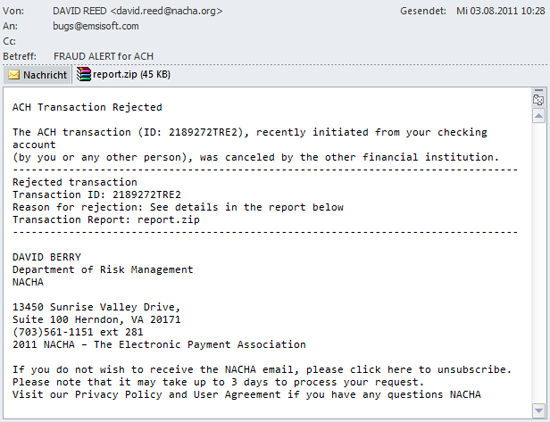
This scam counts on the fact that people will be curious by nature. After all, it obviously involves a bank transfer, and the email includes an attachment. Unfortunately a lot of recipients of such emails overlook the fact that the email doesn’t address them personally and that they probably don’t even have a transfer pending. The layout of email doesn’t look very professional either.
What’s interesting here is the scammer’s intention: they want you to open the attached ZIP file which is disguised as a PDF file. Once you open the ZIP file, it will contain the executable file report485770.pdf.exe which is also disguised as a PDF file.
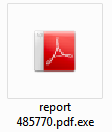
The scammer has even gone to the trouble of providing an Adobe Acrobat icon for the file. Anyone who falls for this trick opens their PC’s door to malware – as the seemingly innocuous file is actually a worm recognized by Emsisoft Anti-Malware as Win32.Garnarue.
How to protect yourself
All these examples are genuine and weren’t recognized by the spam filters in common email programs like Microsoft Outlook or Thunderbird. Therefore the risk to you is very high and not to be taken lightly, considering that it’s primarily your wallet or the security of your PC and data that are under threat.
Incoming mails should always be analyzed before opening any attachments or links. Please keep the following points in mind:
- What email address is present in the “To” field? If the mail isn’t addressed to your exact address, it is highly likely to be a scam.
- The email address of the sender should also be logical. Most companies use formats such as [email protected] or at least general addresses such as [email protected] or [email protected].
- Are you addressed by name? Mail-order companies, friends and family members usually know your name and will therefore send you personalized emails.
- Is the layout professional and does it reflect the company’s identity? Legitimate senders pay attention to style and visual appearance whereas scammers generally don’t. Emails containing many spelling errors are particularly likely to be phishing attempts.
- Do the included links really take you to the company’s website? When moving your mouse over a link, you can clearly see the target address. If the address looks suspicious: Stay away!
- What type of file is attached to the email? You will usually receive PDF or DOC files, as there is no need to compress them into ZIP files. Never run any exe files! Please always pay attention to file extensions.
The more of these points that don’t add up, the more likely it is that the email is a scam. You can also actively protect yourself by following these three rules:
- Choose to display emails as “plain text” rather than HTML. This will make a few emails display oddly, but will enable you to immediately recognize fake links.
- If an email asks you to log into your account or contact a certain company, don’t click on any links or open any attached files. Instead, enter the address of the corresponding company into your browser manually. If in doubt, just get in touch with a customer service representative, as they can enlighten you on the authenticity of an email.
- Use anti-virus software with real-time protection.
Emsisoft Anti-Malware, for example, protects you in three ways by blocking malware before it can be executed using the powerful dual-engine scanner and behavioral analysis. In addition, the surf protection blocks access to many phishing sites when you try to access them.
Have a nice (malware-free) day!
Your Emsisoft Team



