Backgrounds of the current Twitter Spam mails increase
Most Internet users know of Twitter. It is a free service that allows the creation and following of short text messages, like a kind of “World Wide Web TXT”. A lot of private persons, but even huge companies use Twitter. Yes, Twitter is well known and a shining light of the Internet and its possibilities.
But where there is light, there is naturally shadow as well. Our analysis experts at Emsisoft were able to detect a massive outbreak of faked Twitter mails in the last few days, you may have even received one of these emails yourself!
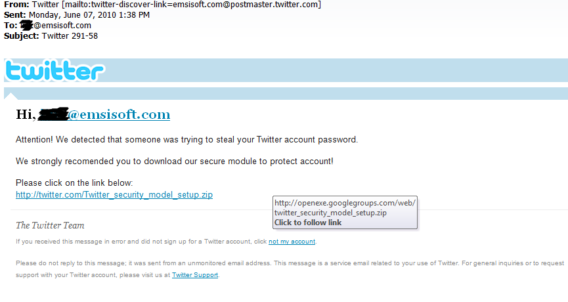
Fake Email
What is behind all this?
The interesting thing is that this email was sent in English, even though it was also sent to people who speak different languages such as German or French. There are translations of Twitter for these languages as well. As the previously mentioned mails are a sort of Phising attempt in most cases, we analyzed this topic in detail.
Also interesting is the use of the recipients Email address. The addresses for Spam attacks like this are usually harvested websites or other infected PCs. Then of course the correct name is not deposited in most cases, so the Email address or parts of it are being used for the initial greeting. For Example: Your Email address is [email protected], which means “Hello, john.doe” will be used.
Some more reliable evidence for this not being an official Email from Twitter is the outbound link. The reader of the message is requested to visit this link in order to install a security module, as someone has apparently repeatedly tried to steal your password. However the link does not lead to Twitter… Despite the fact that the link text is twitter.com, the link itself leads to a different website entirely. We accessed the website for you from a secure Computer.
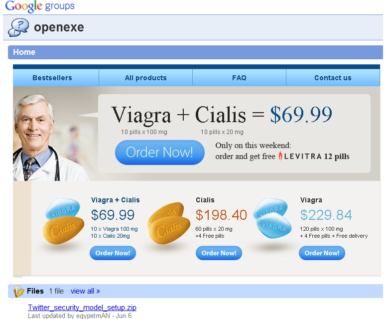
By now, the alarm bells should be ringing. Would the website of a world wide known company look like this, especially regarding such a sensible topic like your password? We can assure you it wouldn’t.
But as we want to show you what happens when you continue to follow this link, our analysis experts went on playing the game. We opened the file “Twitter_security_model_setup.zip” – let us mention that the scan engine of Emsisoft was one of the very first that detected this obvious Malware.
The malware drops some randomly named files such as topwesitjh. A search made on the name brings out references of rogue security software, and we experienced this in our lab as well. On execution, the Malware drops a rogue security software product. Here are some screenshots of the Malware’s payload…
- Creates following files on the desktop
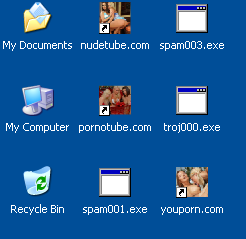
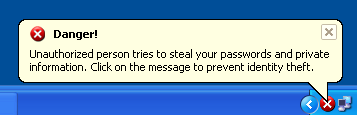
- Fake warnings through a balloon like popup starts appearing.
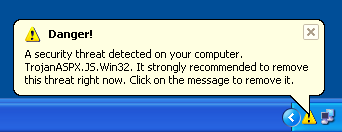
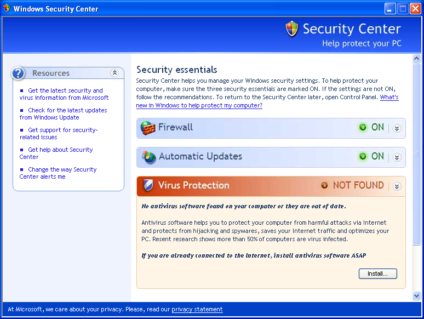
- Replaces Security Center with a fake resemblance – of course the “Install” button does not lead to real security Software.
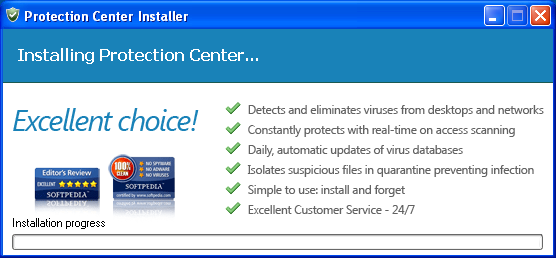
- … but to another Rogue Security Software. After being threatened by all of these fake alerts, will be prompted to buy the fake program.
So you can now see the target of this “infection chain” – the fooled user is almost forced to spend money in the end. Money for a program that stops the fake and self-initiated warnings without offering protection against real Malware. Then the next infection is just a matter of time. By the way, in case you are interested in the Rogue Security Software topic, feel free to have a closer look at the article “Rogue Anti-Spyware“.
Why? – how can I protect myself?
The target that criminals are aiming for is crystal clear: money. After all you are scared into paying for the Rogue Security Program.
You see it is very important to that you are not only safe from Trojans, Viruses, Worms and so on, but even those fake impersonations. An important step to avoid this it to take a closer look at the Emails you receive. Sadly they always look a bit different, we have seen many variants. Additionally, all big and well known names are good for the cheaters – so there have been faked Emails from Amazon, DHL, eBay and Facebook in the past.
All of these emails have some things in common. When you see a message from Twitter or another large company in your Inbox, please watch out for the following:
- Is the mail written in English even though you use the website in a different language?
- Am I addressed with my real name or the alias used in your email address?
- Are there news about real security problems on the Internet? If there would be real attacks on Twitter accounts, some websites should be reporting about this.
- Does the mail look formal, is there a real signature? Every company has its very own style that can be found also in Emails.
- If there is a link, does it really lead to the according website?
- Pay attention to attachments: apart from invoices most company’s do not send attachments. You might see files with names like “filename.pdf.exe” so the recipient thinks it is a PDF, but in fact it is an executable file.
It is possible that some of those points may occur in a legitimate email, but when additional point apply, you are more likely to be conned. If the latest when you see massive warning popups you should be aware of the fact that you probably have Malware on your PC. Windows will probably never suggest a certain security program – unless it is from Microsoft.
You can definitely play it safe by using a security product that offers real time protection, Emsisoft Anti-Malware would have already detected the “Twitter Malware” by its signature. And even without a signature the behaviour analysis recognized the suspicious characteristics during the pests installation.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialFrom our Security Blog: https://blog.emsisoft.com


