Top 10 Ways PUPs Sneak Onto Your Computer. And How To Avoid Them.


We have talked about Potentially Unwanted Programs (PUPs), what they are and how they are even brought to you by free antivirus providers. This article goes into more detail on how PUPs are delivered. Again, any application can be considered potentially unwanted when it is installed without a knowledgeable user’s “proper consent”.
However, with thousands of new PUPs a day and the gray area in which PUPs operate (between annoying and malware), there is still a slight chance that you ever come across a PUP. You may recognize a few methods of how they might sneak in:
Example 1: Spreading through download portals
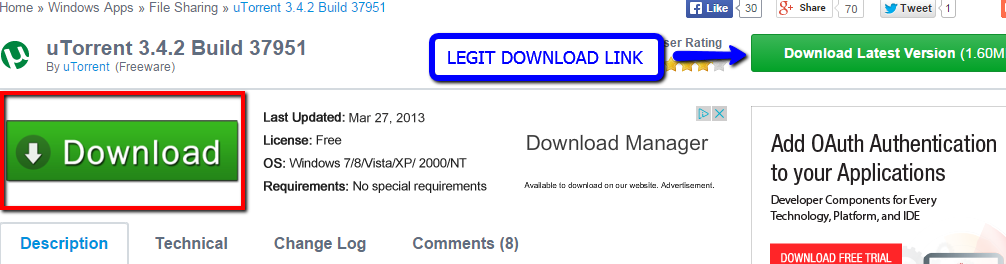
Upon visiting Filehippo.com, one of the most widely used download portals, one can find themselves presented with the most beautiful green download buttons that I have ever seen. However, the case is not so beautiful whenever you find yourself selecting the fake download option presented. Below is a continuation of what happens.
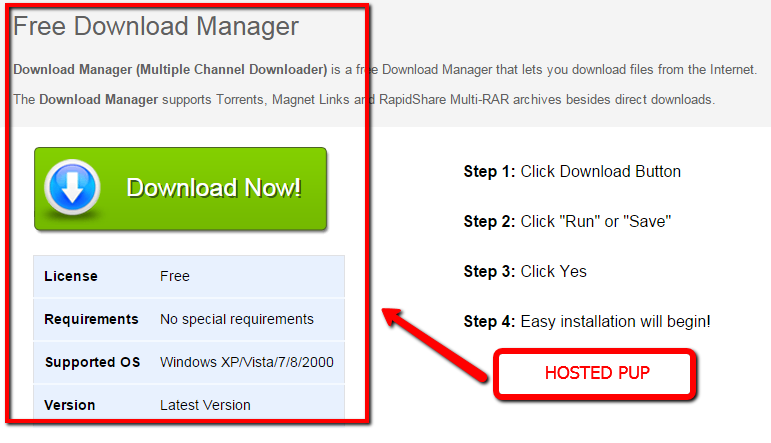
Hmm…. This is interesting, now I am presented with the opportunity to receive a “Free Download Manager”….Wow! This is very nice of “Filehippo”. I really want to install Utorrent…on with the show.
Wait a minute – I wanted Utorrent but this does not look like Utorrent… I wonder what I did wrong?
This presented scenario is a very common method in which users are tricked everyday into downloading PUP’s. A popular download portal hosts freeware software. Sure, the software is “free” (and free is good, right?). You click download and aren’t paying attention or are not aware of the difference in the direct download as compared to the supposed second seemingly legit download option. Congratulations, the PUP infestation has started!
But fear not, there is a work-around.
![]() How to avoid: The best way to avoid PUP scams such as this is to avoid download portals altogether. If you do, pay very close attention when downloading files, use an up-to-date antivirus with PUP detection enabled, and observe the file name and check to be sure it is the software that you are wanting. If it doesn’t have the proper executable name such as Utorrent, don’t execute it.
How to avoid: The best way to avoid PUP scams such as this is to avoid download portals altogether. If you do, pay very close attention when downloading files, use an up-to-date antivirus with PUP detection enabled, and observe the file name and check to be sure it is the software that you are wanting. If it doesn’t have the proper executable name such as Utorrent, don’t execute it.
Example 2: Via fake updates, often pushed through temporary sites
Updates are often pushed through temporarily created websites, developed for Adsense, that serve mostly Open Source software, wrapped in downloaders that prompt users to update their Flash Player, Java, Service Pack etc. There are companies that create hundreds of sites a day in order to mislead the user and generate traffic to their site.
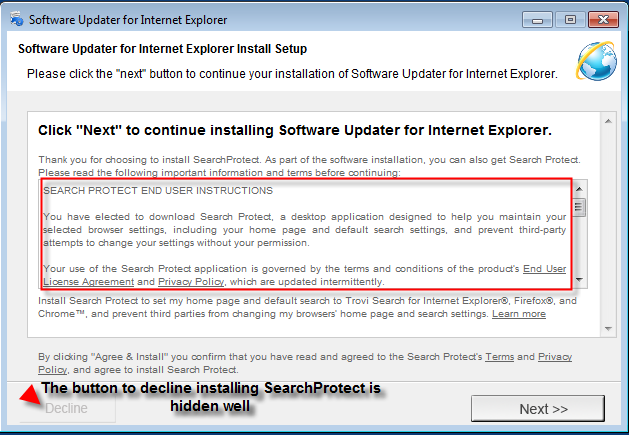
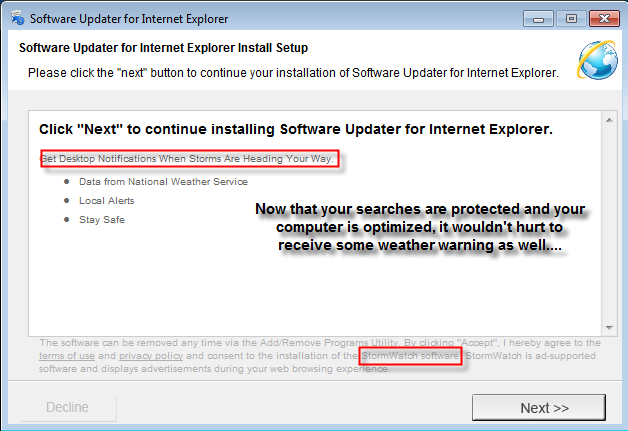
An example: Finally, just what Internet Explorer users have been wanting, an updater for their Internet Explorer. I wonder will this IE updater always ensure that I have the latest version of Internet Explorer. Wait, this definitely doesn’t look like a software updater. This is nice of Internet Explorer to offer me search protection and show me desktop notifications about the weather. Wow, this updated version of IE is really going to be something else!
The two installers above make the user friendly offers. However, the offers that are in the above installations are far from great or friendly. Once installed, Search Protect will change your browser settings (Search Engine, Home Page, Tab Settings) and even submit some of your browsing information to unknown sources. The StormWatch software (which is just adware in disguise) will offer you ads during browsing sessions and more than likely numerous unwanted pop ups about “the weather”. Beware! Fake updaters will possibly “update” your computer status to potentially unwanted!
![]() How to avoid: It can safely be stated that user’s do not want updated software or weather reports from this updater. The best way to avoid this specific installation type junkware is to click Decline and untick any checkboxes which may be present. Once again be sure to USE CAUTION!
How to avoid: It can safely be stated that user’s do not want updated software or weather reports from this updater. The best way to avoid this specific installation type junkware is to click Decline and untick any checkboxes which may be present. Once again be sure to USE CAUTION!
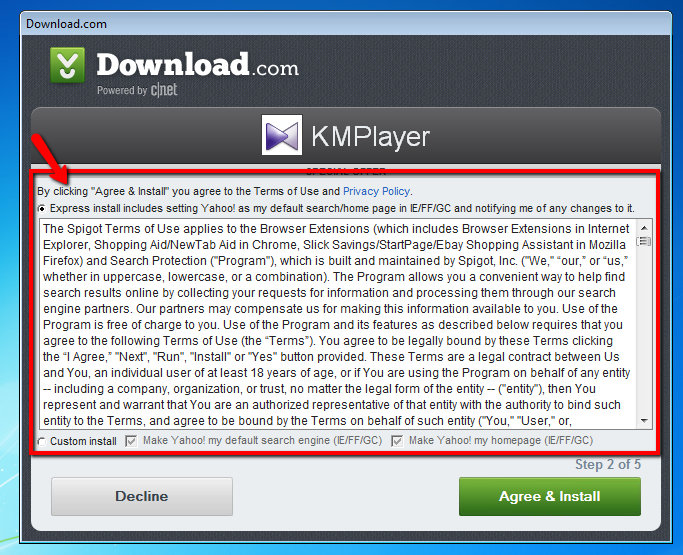
Example 3. Installers: spreading by downloaders and EULA’s
One of my most favorite software programs of all time… KMPlayer. Whoa, this sure is a lot to read! I believe I will just hit Agree and Install! BAM! Now Spigot will install browser extensions, Shopping Aid, NewTab, Ebay Shopping Assistant, and Search Protect. That’s not all – your browser home page and search engine will be changed to Yahoo.
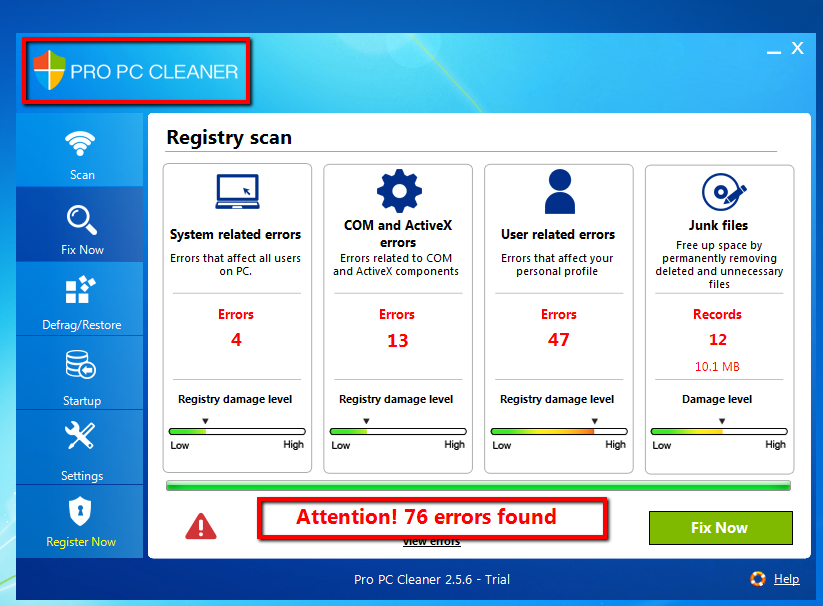
This is the second wave of potentially unwanted “special offers” before finally reaching the legitimate installer. Pro PC Cleaner, will install silently on a PC and then bombard you with fake results annoying the user in many ways. Offers within downloaders (also called wrappers) from sites such as Download.com, Filehippo, Brothersoft, and so forth try to push users into installing and accepting to install junk. A user will not feel like reading a bunch of nonsense. Users only want to install their desired software.
![]() How to avoid: A method of avoiding these types of potentially unwanted programs is to safely hit the decline button, read carefully, and do not install anything without first reading, looking and reading what is being pushed. Also, check on the download portal for information on the specific installer for details on what may be bundled with the software.
How to avoid: A method of avoiding these types of potentially unwanted programs is to safely hit the decline button, read carefully, and do not install anything without first reading, looking and reading what is being pushed. Also, check on the download portal for information on the specific installer for details on what may be bundled with the software.
Example 4: PUP over PUP: one PUP downloads another?
Based upon research, Pro PC Cleaner is a very common potentially unwanted program that is bundled with freeware on many download portals. I wonder how effectively it can really clean a PC? In theory, this PUP can be similarly compared to a rogue product. Lets investigate:
The above PUP was actually downloaded in the background by accepting the EULA agreement terms in the Download.com downloader for KMPlayer. It is a truly frightening scenario; however, it is very true. One potentially unwanted program downloads another. Pro PC Cleaner is attempting to fool the user into purchasing their paid version (similar to a rogue). Just one install from Download.com and already an annoying PUP popping up.
![]() How to avoid: Remember to stay sharp, use common sense, and carefully observe and read EVERYTHING before installing. As mentioned earlier, please ensure your antivirus is up to date with PUP detection enabled.
How to avoid: Remember to stay sharp, use common sense, and carefully observe and read EVERYTHING before installing. As mentioned earlier, please ensure your antivirus is up to date with PUP detection enabled.
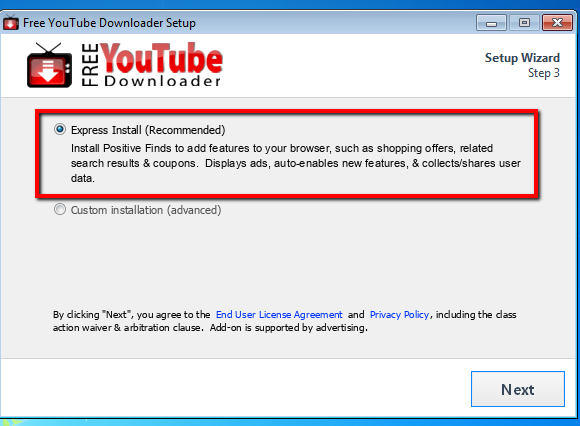
Example 5: Express Installation: the express way to get infected?
In this example, we’re using Free Youtube Downloader, which is a very popular freeware application on CNET.com for downloading videos from Youtube. However, I bet CNET doesn’t inform the user about potentially unwanted offers inside. Let’s take a look:
There you have it. The express way is not always the best method to take. Yes, the Express installation process may be only a few clicks and done; however, is it really worth the risk of installing potentially unwanted programs? Skype is a legitimate application; however, it may be unwanted for a user that doesn’t need it. The express installation installed potentially unwanted programs to the browser which will display ads and collect/share user data. That doesn’t sound too friendly to me.
![]() How to avoid: Never use the express or recommended installation. It’s recommended with the best interest of the creator in mind, not yours.
How to avoid: Never use the express or recommended installation. It’s recommended with the best interest of the creator in mind, not yours.
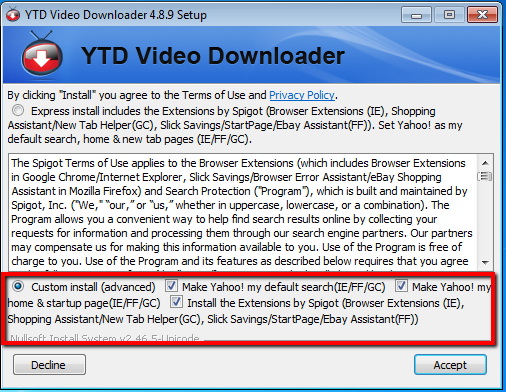
Example 6: Custom Installation: is a custom install better than express?
YTD video downloder is yet another popular freeware application. Lets check to see if its installation options are any less PUPish on its custom install than Free Youtube Downloader. Will the custom install make a difference? Lets Find Out:
It does not take a rocket scientist to see that while custom installation options are available, the potentially unwanted programs are too sadly. However, there is a distinct difference between Express and Custom install options: an express install does not give the user an option to change what you want installed, while a custom installation lets a user choose exactly what is being installed on their system. A user can easily uncheck all unwanted offers if they are cautious and do not take the express way.
![]() How to avoid: Use the same tactics mentioned before with the inclusion of also choosing a custom install option. As mentioned above, choosing a custom install is wisely recommended because then you control what is installed on your system. Always, try to choose a custom install when available.
How to avoid: Use the same tactics mentioned before with the inclusion of also choosing a custom install option. As mentioned above, choosing a custom install is wisely recommended because then you control what is installed on your system. Always, try to choose a custom install when available.
Example 7: New homepage, search engine and updated drivers
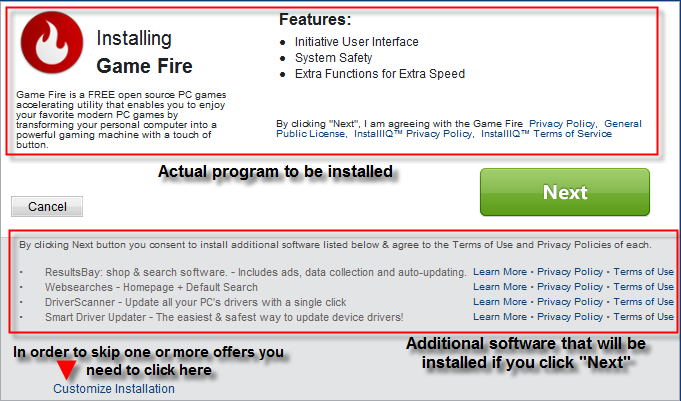
Under normal circumstances, the ability to change one’s browser homepage and search engine is good. However, potentially unwanted programs now utilize methods of deceit within installers to trick a user to changing a home page, search engine and even new tab settings. Customized installations are even victims to this devilish PUP trickery as shown below.
As shown in the above screenshot, a user will be prompted with several potentially unwanted offers. In the image we see: Game Fire, ResultsBay, WebSearches, Driver Scanner, and Smart Driver updater all occuring from one simple installation. Wow! That is a lot to take in! PUP’s are taking over installers. Proceed with caution! Custom installations are no longer as “secure” as people believe them to be.
![]() How to avoid: Having the ability to avoid these types of offers is critical. Carefully untick all the checkboxes that appear to install junkware. You may even hit cancel with some installers that may cancel the PUP installation. Again, it is stressed that you be very careful and read installation options before proceeding.
How to avoid: Having the ability to avoid these types of offers is critical. Carefully untick all the checkboxes that appear to install junkware. You may even hit cancel with some installers that may cancel the PUP installation. Again, it is stressed that you be very careful and read installation options before proceeding.
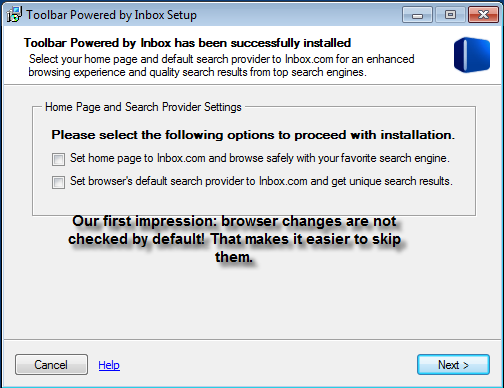
Example 8: Spread by force: the almost no way out method
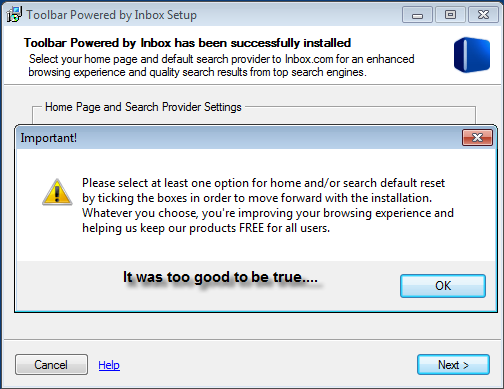
The activities performed by this potentially unwanted offer is anything but fun. In summary, Inbox toolbar wants to install as a typical PUP; however, this PUP is playing dirty. The inbox toolbar installation is actually willing to force the user to make a change to their home page or search provider before installing the software. Sounds like the user needs to send this toolbar to the deleted folder!
Never fear, there is hope! It seemed very grim and dark for a moment. The above so called forceful potentially unwanted offers can be skipped over indeed. This PUP was trying with all of its cunningness to trick the user into changing their browser settings. This type of PUP above should be approached and dealt with cautiously before proceeding with the rest of the installation.
![]() How to avoid: In order to avoid this installation, one must always use good judgement and choose to untick the potentially unwanted checkboxes . Additionally, it may be possible to select cancel in order to skip over the offer as well. NEVER proceed through an installation without cautiously reading what is being offered. Users may assume that at this point, it may be a wise decision to cancel out of the installation altogether.
How to avoid: In order to avoid this installation, one must always use good judgement and choose to untick the potentially unwanted checkboxes . Additionally, it may be possible to select cancel in order to skip over the offer as well. NEVER proceed through an installation without cautiously reading what is being offered. Users may assume that at this point, it may be a wise decision to cancel out of the installation altogether.
Example 9: Someone else uses your computer
You may share your computer with your kids, co-worker or significant other. They may not be as careful as you and get you PUPs on their computer. This could especially be the case if they visit torrent sites, streaming sites or online gaming sites which frequently bombard you with downloads and ads.
![]() How to avoid: The only way to really get around this is, is to use your computer for your own use only.
How to avoid: The only way to really get around this is, is to use your computer for your own use only.
Example 10: Your employer lets you do research on PUPs ;)
Even if you are like me and pay close attention to what you’re installing, it still can be very tricky. Some PUP creators are working hard to get around antivirus programs and uninstall programs, sometimes with a simple line of code. Some PUPs are really hard to detect by a savvy computer user, let alone the average computer user.
![]() How to avoid: Use a virtual machine and/or take a recovery snapshot of your operating system before starting your research. This might sound a bit over-the-top, but really is a straightforward way to not have to worry about how slow your system – even if it is just your computer at work – might end up.
How to avoid: Use a virtual machine and/or take a recovery snapshot of your operating system before starting your research. This might sound a bit over-the-top, but really is a straightforward way to not have to worry about how slow your system – even if it is just your computer at work – might end up.
How to avoid PUPs: Important facts to remember
In the end, everyone will succumb to at least one potentially unwanted program in their life. The industry needs to change and take a clear stance on PUPs, so that they’re only offered opt-out or so that antivirus programs can block them all. The important facts to remember to avoid potentially unwanted programs is:
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trial- Be cautious, use common sense and take your time.
- Install, update, and run a reputable antivirus software, such as Emsisoft Anti-Malware that offers real-time protection against PUPs.
- Only use reputable download sources.
- NEVER download or install applications that seem suspicious or malicious.
- Look for custom installation options and use them if available.
- Look for concealed Decline/Skip buttons, usually they have an unobtrusive font type and color contrary to the big shiny “Next” button.
- Scan and clean your computer from PUPs periodically with our the Free Emsisoft Emergency Kit.
Have a great (PUP-free) day!