Ransomware Profile: BlackMatter

BlackMatter is a strain of ransomware that encrypts files and threatens to leak stolen data if the ransom is not paid. The group targets large companies with annual revenues of more than $100 million and is actively recruiting affiliates as it ramps up its operations. BlackMatter may be a rebrand or spinoff of the now-defunct cybercrime outfit DarkSide due to the unique encryption routines employed by both ransomware groups.
What is BlackMatter?
BlackMatter is a ransomware variant that encrypts files using Salsa20 and 1024-bit RSA encryption and demands a large sum of cryptocurrency for their decryption.
As with many other ransomware groups, BlackMatter uses the threat of data exposure to increase the chances of achieving a payout. Before executing the final ransomware payload, BlackMatter operators exfiltrate data from compromised systems and threaten to release it on the group’s leak site unless the victim pays the ransom.
BlackMatter operates as a ransomware-as-a-service (RaaS), a business model in which affiliates earn a portion of ransom payments in exchange for dropping the malware onto compromised systems. BlackMatter also works with initial access brokers, individuals who are willing to sell access to compromised networks. Initial access brokers are paid $3,000 – $100,000 for network access, depending on the target.
Possible link between BlackMatter and DarkSide
DarkSide is the ransomware gang responsible for the Colonial Pipeline attack in May 2021 that resulted in fuel shortages and price spikes across the U.S. Following unprecedented pressure from U.S. and Russian authorities, DarkSide was forced to shut down its operations a few weeks later.
There is some evidence to suggest that DarkSide, or at least some members of DarkSide, may have returned under the BlackMatter moniker. After investigating a leaked BlackMatter decryptor, Emsisoft analysts determined that BlackMatter uses the same encryption routines that DarkSide formerly used in their attacks, including a custom Salsa20 matrix that was unique to DarkSide.
The history of BlackMatter
BlackMatter was first observed in late July 2021, when the alias “BlackMatter” was registered on the Russian-language cybercrime forums XSS and Exploit. The user deposited 4 bitcoins (worth approximately $150,000 USD at the time) into its Exploit escrow account, signaling their legitimacy and seriousness as a threat actor. Shortly after, the user posted an advertisement offering initial access brokers $3,000 – $100,000 for access to corporate networks that met the group’s criteria.
In early September 2021, the U.S. Department of Health and Human Services’ Health Sector Cybersecurity Coordinating Council issued a threat brief on BlackMatter.
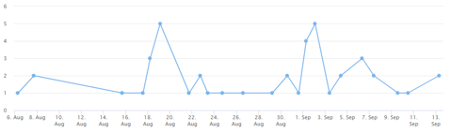
Since BlackMatter was first discovered, there have been 44 submissions to ID Ransomware, an online tool that helps the victims of ransomware identify which ransomware has encrypted their files. We estimate that only 25 percent of victims make a submission to ID Ransomware, which means there may have been a total of 176 BlackMatter incidents since the ransomware’s inception. During this time, the group has also published on its leak site the stolen data of 10 organizations.
BlackMatter ransom note
After the encryption process is complete, BlackMatter drops a ransom note in user-accessible folders and changes the desktop wallpaper to a ransom notice. Some versions of the ransomware also print a physical copy of the ransom note by sending a print job from each infected endpoint to the default printer.
The ransom note states that the victim’s files have been encrypted and provides instructions on how to communicate with the attackers. The note also specifies the type of data that was stolen during the attack, along with a “guarantee” that the threat actors will uphold their end of the bargain by decrypting the victim’s files and deleting the exfiltrated data after receiving payment.
Below is a sample BlackMatter ransom note:
BLACK
Matter
>>> What happens?
Your network is encrypted, and currently not operational. We have downloaded 1TB from your fileserver.
We need only money, after payment we will give you a decryptor for the entire network and you will restore all the data.
>>> What guarantees?
We are not a politically motivated group and we do not need anything other than your money.
If you pay, we will provide you the programs for decryption and we will delete your data.
If we do not give you decrypters or we do not delete your data, no one will pay us in the future, this does not comply with our goals.
We always keep our promises.
>> Data leak includes
- Full emloyeers personal data
- Network information
- [REDACTED]
- Finance info
>>> How to contact with us?
- Download and install TOR Browser (hxxps://www.torproject.org/).
- Open [URL REDACTED].
>>> Warning! Recovery recommendations.
We strongly recommend you to do not MODIFY or REPAIR your files, that will damage them.
Who does BlackMatter target?
BlackMatter targets large, well-resourced organizations. The group has attacked organizations located in the U.S., the U.K., Canada, Australia, India, Brazil, Chile and Thailand, although the list of impacted countries is growing.

The BlackMatter group has developed versions of its ransomware for both Windows and Linux, enabling attackers to attack Linux-based environments including ESXi, Ubuntu, Debian and CentOS.
BlackMatter claims that it does not attack certain industries as doing so would attract unwanted attention. This includes:
- Hospitals
- Critical infrastructure facilities (nuclear power plants, power plants, water treatment facilities)
- Oil and gas industry (pipelines, oil refineries)
- Defense industry
- Non-profit companies
- Government sector
If an entity in one of these industries is attacked (perhaps inadvertently or by an incautious affiliate), the group claims that it will provide free decryption.
As always, any claims made by cybercrime groups should be met with skepticism. In addition, even if the group does provide free decryption to an impacted entity, recovery may still take days, weeks or months to complete. Such incidents can result in substantial disruption and financial loss; in the healthcare sector, it can mean loss of life.
How does BlackMatter spread?
BlackMatter attacks begin by breaching the target network, usually via compromised remote desktop protocol, phishing campaigns, exploiting known vulnerabilities or stolen credentials.
When BlackMatter is executed, it verifies the rights of the current user. If privileges are restricted by User Account Control, the malware attempts to escalate its privileges using the ICMLuaUtil COM interface. This same technique is used by DarkSide and LockBit. After gaining the necessary privileges, BlackMatter terminates a number of productivity-related processes and deletes volume shadow copies of the targeted directories. Before the encryption begins, attackers also exfiltrate data, which is used as additional leverage to pressure victims into paying the ransom.
During encryption, BlackMatter attempts to mount and encrypt unmounted partitions. It targets files stored locally and on network shares, as well as removable media, while ignoring specific directories, files and file extensions that are necessary for the device to function.
As BlackMatter operates as a RaaS and can be distributed by many different affiliates, the exact anatomy of an attack can vary from incident to incident.
Major BlackMatter attacks
- Olympus: In September 2021, Japanese tech giant Olympus was hit with BlackMatter. After detecting suspicious activity on its networks in Europe, Africa and the Middle East, the company was forced to suspend data transfers in the affected systems as a precautionary measure. A specialized response team was mobilized to resolve the issue.
How to protect the network from BlackMatter and other ransomware
The following practices may help organizations reduce the risk of a BlackMatter incident.
- Cybersecurity awareness training: Because the majority of ransomware spreads through user-initiated actions, organizations should implement training initiatives that focus on teaching end users the fundamentals of cybersecurity. Ransomware and propagation methods are constantly evolving, so training must be an ongoing process to ensure end users are across current threats.
- Credential hygiene: Practicing good credential hygiene can help prevent brute force attacks, mitigate the effects of credential theft and reduce the risk of unauthorized network access.
- Multi-factor authentication: MFA provides an extra layer of security that can help prevent unauthorized access to accounts, tools, systems and data repositories. Organizations should consider enabling MFA wherever possible.
- Security patches: Organizations of all sizes should have a robust patch management strategy that ensures security updates on all endpoints, servers, and appliances are applied as soon as possible to minimize the window of opportunity for an attack.
- Backups: Backups are one of the most effective ways of mitigating the effects of a ransomware incident. Many strains of ransomware can spread laterally across the network and encrypt locally stored backups, so organizations should use a mixture of media storage, and store backup copies both on- and off-site. See this guide for more information on creating ransomware-proof backups.
- System hardening: Hardening networks, servers, operating systems and applications is crucial for reducing attack surface and managing potential security vulnerabilities. Disabling unneeded and potentially exploitable services such as PowerShell, RDP, Windows Script Host, Microsoft Office macros, etc. reduces the risk of initial infection, while implementing the principle of least privilege can help prevent lateral movement.
- Block macros: Many ransomware families are delivered via macro-embedded Microsoft Office or PDF documents. Organizations should review their use of macros, consider blocking all macros from the Internet, and only allow vetted and approved macros to execute from trusted locations.
- Email authentication: Organizations can use a variety of email authentication techniques such as Sender Policy Framework, DomainKeys Identified Mail, and Domain-Based Message Authentication, Reporting and Conformance to detect email spoofing and identify suspicious messages.
- Network segregation: Effective network segregation helps contain incidents, prevents the spread of malware and reduces disruption to the wider business.
- Network monitoring: Organizations of all sizes must have systems in place to monitor possible data exfiltration channels and respond immediately to suspicious activity.
- Penetration testing: Penetration testing can be useful for revealing vulnerabilities in IT infrastructure and employees’ susceptibility to ransomware. Results of the test can be used to allocate IT resources and inform future cybersecurity decisions.
- Threat hunting: As malicious actors may be present on the network for some time before deploying the ransomware payload, organizations should engage in preemptive threat hunting. This involves establishing a baseline of the IT environment’s routine activity, and regularly reviewing data logs to identify anomalous activity. Intrusion prevention systems, automated security alert systems and honeytokens may also be useful in detecting suspicious activity.
- Incident response plan: Organizations should have a comprehensive incident response plan in place that details exactly what to do in the event of infection. A swift response can help prevent malware from spreading, minimize disruption and ensure the incident is remediated as efficiently as possible.
How to remove BlackMatter and other ransomware
BlackMatter uses encryption methods that currently make it impossible to decrypt data without paying for an attacker-supplied decryption tool.
Victims of BlackMatter should be prepared to restore their systems from backups, using processes that should be defined in the organization’s incident response plan. The following actions are recommended:
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free Trial- Take action to contain the threat.
- Determine the extent of the infection.
- Identify the source of the infection.
- Collect evidence.
- Restore the system from backups.
- Ensure all devices on the network are clean.
- Perform a comprehensive forensic analysis to determine the attack vector, the scope of the incident and the extent of data exfiltration.
- Identify and strengthen vulnerabilities to reduce the risk of a repeat incident.


