How we use the Swiss cheese model to prevent malware infections
Whether you’re dealing with malware or COVID, there’s no singular action that can prevent infection.
Every preventative measure has its flaws and limitations. The best signature-based malware scanner, for example, will eventually allow a zero-day threat to slip through, while even the most conscientious hand-washer won’t be able to reliably scrub off every germ every time they turn on the faucet.
Combine the signature-based scanner with behavior-based protection, however, and the chance of malware infection drops considerably. Similarly, encourage the hand-washer to also steer clear of crowds, and their risk of catching a disease decreases.
The Swiss cheese model is based on this simple principle of layered protection – and it holds the key to preventing COVID, malware and hundreds of other hazardous events.
What is the Swiss cheese model?
Originally developed in 1990 by Dante Orlandella and James Reason of the University of Manchester, the Swiss cheese model of accident causation is a theoretical model used in risk analysis and the principle behind layered security. It offers a useful way to visualize how accidents occur only when every layer of a defense system fails, and is used in a wide range of accident-prone industries, including aviation, engineering, healthcare, emergency services and more.
In the Swiss cheese model, an organization’s defenses against failure are represented by slices of cheese, while the holes in the slices – which vary in size and position in each slice – represent weaknesses in individual parts of the system. Failure occurs when the holes in the slices align, allowing a hazard to pass through all of the layers of defense.
How can the Swiss cheese model be applied to COVID?
As a widespread, contagious and sometimes asymptomatic disease, there’s no single intervention that can prevent the spread of COVID. A face mask, for example, won’t protect you if you happen to touch an infected surface and forget to wash your hands. Similarly, mandating social distancing may not be effective if a building has poor ventilation.
Every recommended preventative measure makes you safer – but none of them make you safe. The Swiss cheese model shows how multiple layers improve the chance of success. The more barriers you have – the more slices of cheese in your COVID defense system – the higher the chance of preventing infection.
Cheese slices for preventing COVID
- Personal hygiene:
- Masks
- Hand washing
- Social distancing
- Coughing/sneezing etiquette
- Administrative controls:
- Adoption of remote working
- Restrictions on the use of small spaces
- Engineering controls:
- Air filtration in buildings
- Increase in outside-air ventilation
- Government efforts:
- Quarantine and isolation
- Closure of non-essential businesses
- Limits on social gatherings
- Contact tracing
- Financial support
- Healthcare measures:
- Ventilators
- Vaccines
How can the Swiss cheese model be applied to cybersecurity?
The Swiss cheese model can also be applied to infections of the digital variety. As with COVID preventative measures, every cybersecurity solution has its weaknesses, which means there’s no single technology that can reliably protect users from malware.
…there’s no single technology that can reliably protect users from malware.
In cybersecurity, each slice of cheese in the Swiss cheese model represents a layer of protection. The more slices of cheese you have, the greater the chance of stopping malware before it can infect your system. Combining multiple security technologies that address vulnerabilities on both a network and end-user level is crucial for ensuring that all attack vectors are secured, and that threats can be identified and remediated if prevention is not possible.
Cheese slices for preventing malware
- Perimeter security
- Physical barriers
- Digital security systems
- Access control
- Authentication mechanisms
- Network security
- Firewall
- Access control
- VPN
- Segmentation
- Employee awareness training
- How to recognize and respond to threats
- Phishing simulations
- Reporting procedures
- Company IT policies
- Endpoint security
- Antivirus software
- Spam filter
- Multi-factor authentication
- Patch management
- Real-time monitoring
- Threat detection
- Remediation
- Disaster recovery
- Backups
- Continuity plan
- Cyber insurance
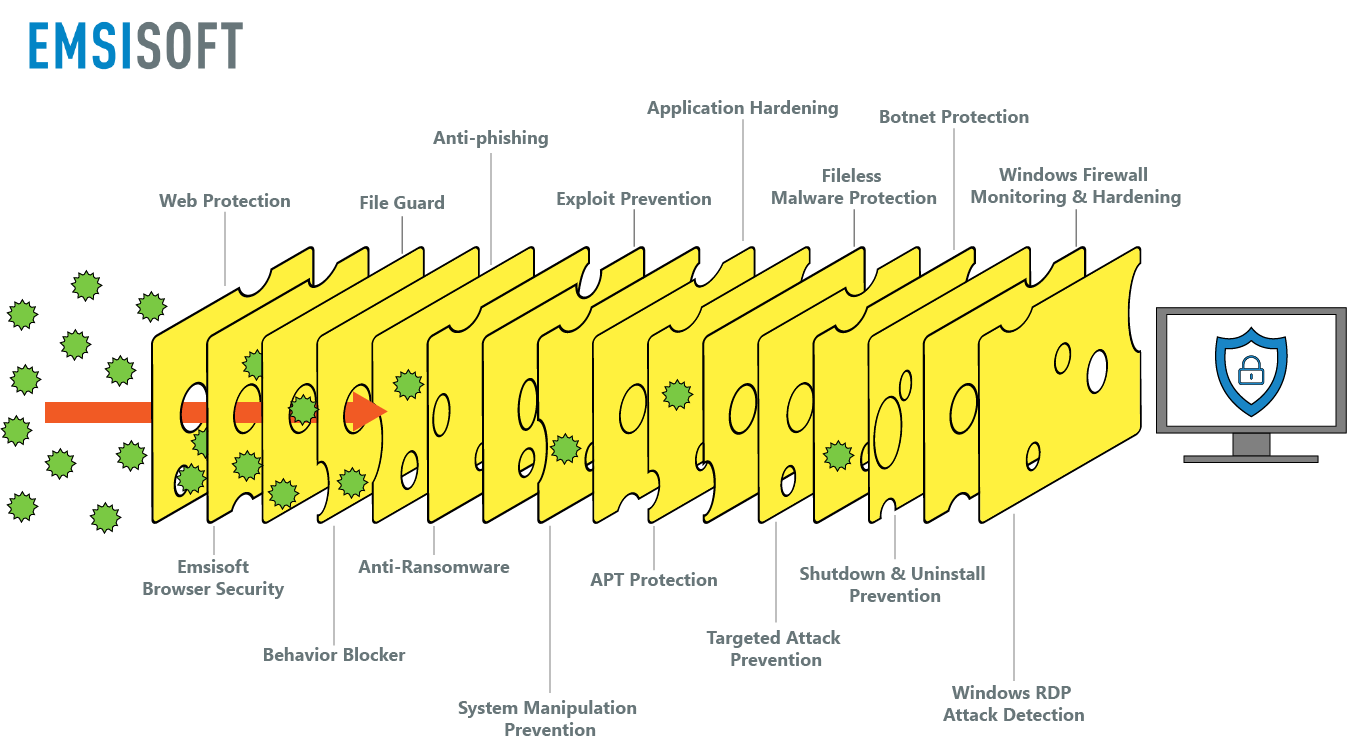
How we apply the Swiss cheese model to Emsisoft solutions
Emsisoft solutions are built based on the principles of the Swiss cheese model. We recognize that no single component can provide 100 percent protection, which is why we use a combination of layered security elements that work in synergy to protect your system from malware.
Here’s how our slices of cheese work together to keep you safe:
- Slice 1 – Web Protection: Web Protection keeps you safe while you browse the web by blocking connections to dangerous hosts. Emsisoft solutions use a huge database of malicious hosts that is updated every 15 minutes to protect you from a range of threats, including malware, phishing, potentially unwanted programs and privacy risks. Web Protection is hostname-based and works at the Windows system level, which means it works with all browsers and doesn’t require updates when new browser versions are released.
- Slice 2 – Emsisoft Browser Security: Designed to complement our Web Protection component, Emsisoft Browser Security is a privacy-conscious browser extension that blocks access to malicious websites that distribute malware and prevents phishing attacks. Unlike Web Protection, Emsisoft Browser Security filters at a URL level and works only in your browser.
- Slice 3 – File Guard: If a malicious file manages to slip past your outer protection layers, File Guard will intercept and remove the threat. Active in the background at all times, File Guard uses a powerful dual-engine scanner to check all files that are downloaded, run or modified against millions of known malware signatures. By default, threats are automatically quarantined with notification.
- Slice 4 – Behavior Blocker: While traditional file scanners are excellent at stopping known threats, they are unable to detect freshly created malware variants. That’s where the Behavior Blocker comes in. The Behavior Blocker sits between your operating system and the applications on your system and looks for malicious behavior patterns. When suspicious behavior is detected, the Behavior Blocker interrupts the activity and raises the alert. Because there are only so many ways that malware can behave, the Behavior Blocker can detect almost any type of malware – even if it has never before been seen in the wild.
- Slice 5 – Anti-phishing: The Anti-Phishing component blocks access to websites that are known to try to steal your login credentials and banking information. Unlike some cybersecurity vendors, our anti-phishing technology does not involve HTTPS interception, which can potentially impact your privacy. See this article for more information.
- Slice 6 – Anti-Ransomware: Ransomware is one of the most serious – and most costly – cyber threats facing organizations today. Using custom-built behavioral monitoring, the Anti-Ransomware component stops ransomware before it can encrypt the first file.
- Slice 7 – Exploit Prevention: Exploit Prevention plays an important role in stopping new infections. It works by preventing exploits from injecting code into foreign programs to execute harmful payloads.
- Slice 8 – System Manipulation Prevention: This layer of protection keeps you safe by stopping the many types of malware that may attempt to manipulate your system, including exe-patchers, hidden rootkits, autoruns, host changers, browser settings changers, group policy changers and invisible installers.
- Slice 9 – Application Hardening: Application Hardening controls potentially dangerous procedures within active programs. For example, Application Hardening can stop commonly attacked software (such as Microsoft Office products) from being able to execute dangerous PowerShell scripts.
- Slice 10 – APT Protection: An advanced persistent threat (APT) is a type of attack in which an unauthorized user establishes a long-term presence in your network (often to exfiltrate data). APT Protection ensures such intruders are detected before they can inflict damage.
- Slice 11 – Fileless Malware Protection: Fileless malware is a type of malware that resides only in memory and never touches your hard drive, which makes detection challenging for some cybersecurity solutions. Emsisoft protection software utilizes a number of technologies that work together to prevent fileless malware infections.
- Slice 12 – Targeted Attack Prevention: Motivated attackers may use highly customized attacks to gain access to your system. This protection component prevents a wide range of targeted attacks, including spear-phishing, single-use malware, state trojans and industrial espionage.
- Slice 13 – Botnet Protection: The Behavior Blocker and signature-based scanner heuristics work in synergy to prevent your devices from becoming part of a botnet. A botnet is a huge collection of compromised devices that threat actors use to conduct malicious activity.
- Slice 14 – Shutdown & Uninstall Prevention: Some types of malware, including many ransomware attacks, work by threat actors disabling the security software on the compromised machine. To prevent this from happening, Emsisoft protection software gives you the option to set a local security admin password. Even if an attacker gains full access to your device, they won’t be able to shut down or uninstall your protection software without the password.
- Slice 15 – Windows Firewall Monitoring & Hardening: Windows Firewall protects your network by filtering out unauthorized traffic. Emsisoft protection software ensures that the Window Firewall is enabled and prevents it from being manipulated by third-party software.
- Slice 16 – Windows RDP Attack Detection: Remote Desktop Protocol (RDP) is a network communications protocol developed by Microsoft. When RDP is not secured properly, threat actors can easily exploit it to gain access to Windows devices and install ransomware and other malware. Windows RDP Attack Detection protects you from this threat by checking if RDP is enabled and alerting you when it is under brute force attack.
The Swiss cheese model is a useful way of showing how accidents happen when flaws in a defense system align – and how accidents can be prevented with additional layers of security.
Whether it’s cybersecurity or disease prevention, taking a layered approach to risk management ensures that one layer’s weaknesses are mitigated by the strengths of another. Combining defense mechanisms provides multiple opportunities for hazards to be intercepted and minimizes the risk of system failure.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free Trial