Petya ransomware variant attacks computers worldwide


Hot on the heels of last month’s Wannacry attack that caught global media attention arrives the latest outbreak of ransomware that is spreading rapidly across Europe and other continents. The culprit? A new variant of the Petya ransomware family, also known as Petna in IT security circles. For the remainder of the article we will refer to the ransomware simply as Petya.
Spotted earlier this morning, the ransomware hit the Ukraine particularly badly, affecting government branches, Kiev airport, the metro system, the state energy provider Ukrenergo, the central bank and even the defunct Chernobyl nuclear power plant.
Further infections have been confirmed by businesses in other parts of Europe, including British ad agency WPP, French construction company Saint-Gobain, Russian oil company Rosneft and Danish shipping giant AP Moller-Maersk. Until now, the ransomware infection has been confirmed in more than 14 countries including the US, Mexico, Iran and Brazil; yet we expect a lot more countries to be affected.
Perhaps most surprising is the fact that this latest Petya ransomware variant uses the same NSA exploits that allowed Wannacry to infect more than 200,000 computers in May this year. Despite security patches and advice that followed, it appears many companies did not heed the advice from security experts.
Will this latest ransomware attack be even worse than Wannacry? And what can be done to secure your computer and networks?
Meet Petya Ransomware
In a way, the latest Petya variant seems to be closely related to the existing Petya ransomware family. Petya was first seen spreading at the end of March 2016. What made Petya unique was the implementation of its own little operating system that it installed and booted instead of Windows, so it could encrypt various critical file system structures on the boot disk during the next restart. The new Petya variant copied this method and even the code of the Petya operating system almost completely but implements its own methods to spread, encrypt files and infect the system.
Following the successful infection of a system, Petya presents a ransom screen, available in English only, asking to pay $300 worth of bitcoins to a wallet connected with a posteo.net address:
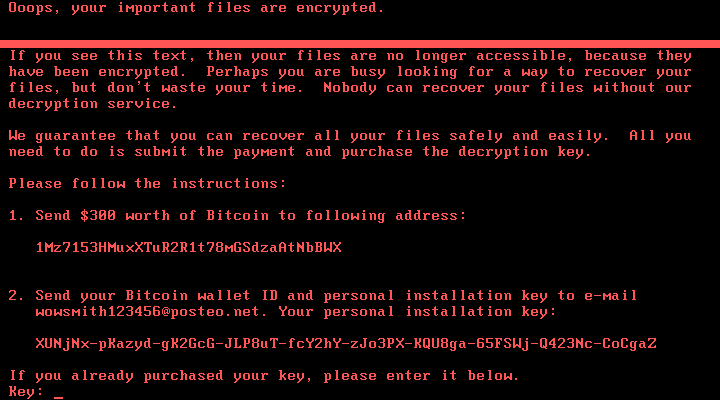
Petya ransom note is displayed once the encryption is complete.
At the time of writing, 4 bitcoins have been paid through 45 transactions, netting the ransomware author more than US$ 10,200. While this amount is comparatively small, it is still early and given the rapid spread, we may see more victim’s paying up to free their files.
How do you get infected with the Petya ransomware?
The initial wave of Petya infections can be traced back to a hack of the popular Ukrainian accounting software vendor MeDoc. Unknown attackers gained access to the software’s update servers and delivered Petya ransomware as a software update to the company’s clients. Similar methods have been used in the past by ransomware families like XData to start off the initial wave of attacks.
Once a number of systems were infected, Petya was able to spread rapidly from there through the same NSA exploit that was leaked by the Shadow Brokers group that was also used by WannaCry. The exploit, known as ETERNALBLUE, exploits a vulnerability in the Microsoft SMBv1 protocol, allowing an attacker to take control over systems which:
- have the SMBv1 protocol enabled
- are accessible from the internet and
- have not been patched by the MS17-010 fix released back in March 2017
If the ETERNALBLUE exploit is successful, it will install a backdoor on the system which is codenamed DOUBLEPULSAR. DOUBLEPULSAR is used by the malware to send itself to the exploited system and then execute itself.
In addition, Petya also uses various administrative features integrated into Windows to spread within a compromised network. This means that a single unpatched machine can be enough to get a whole network infected, even if the other machines are fully patched. Petya uses Windows Management Instrumentation (WMI) and the popular tool PsExec in combination with administrative network shares in order to facilitate the lateral spreading of the ransomware within the local network.
How does Petya ransomware encrypt your files?
Petya consists of two different ransomware modules. The first module is very similar to classical ransomware families. It encrypts up to the first 1 MB of files with one of the following extensions:
.3ds .7z .accdb .ai .asp .aspx .avhd .back .bak .c .cfg .conf .cpp .cs .ctl .dbf .disk .djvu .doc .docx .dwg .eml .fdb .gz .h .hdd .kdbx .mail .mdb .msg .nrg .ora .ost .ova .ovf .pdf .php .pmf .ppt .pptx .pst .pvi .py .pyc .rar .rtf .sln .sql .tar .vbox .vbs .vcb .vdi .vfd .vmc .vmdk .vmsd .vmx .vsdx .vsv .work .xls .xlsx .xvd .zip
To encrypt the files, it uses the AES algorithm with a 128 bit key. That key is then encrypted using an RSA public key embedded within the ransomware executable. More details of how ransomware utilizes RSA and AES to securely encrypt files, can be found in our spotlight article about encryption.
The second module was ripped out straight out of the Petya ransomware family. It consists of a custom little operating system that is installed to the system’s Master Boot Record (MBR), provided that the system is able to boot via MBR and the ransomware managed to gain the required rights. Once the Petya OS boots, it will locate and encrypt the Master File Table of the boot drive using the Salsa20 stream cipher.
The Master File Table is an internal data structure of the NTFS Windows file system. It essentially keeps track of where exactly on the disk the data is located for each file. In addition, the Petya ransomware OS will also encrypt the first sectors of each file, to prevent any file recovery tools from working properly. Without the Master File Table, Windows can’t make sense of the data on the disk, essentially locking the user out from their system completely.
How can I protect myself from Petya ransomware?
Our advice given during the WannaCry attack still holds true in the case of Petya: As an immediate measure, make sure to have the latest security updates installed on your Windows computers and servers. Following the previous ransomware outbreak, Microsoft had taken the unusual step to release security patches for “unsupported systems” such as Windows XP and Windows Server 2003, so even those systems can be patched.
As explained in our ransomware article, the best protection still remains a reliable and proven backup strategy, especially since the encryption used by the Petya ransomware is secure. The only way to get the data back is through the help of the ransomware author or via restoring from backups. Making sure to install critical Windows updates is also a very important step in protecting a system, as Petya’s main infection vector so far is the ETERNALBLUE SMBv1 exploit currently, which has been patched for several months already.
Apart from regular backups, you will be glad to hear that Emsisoft’s Anti-Ransomware module, part of our Behavior Blocker technology and used by Emsisoft Anti-Malware, has proven to be the next best defense.
Watch the video to see Emsisoft Anti-Malware in action against Petya ransomware:
It catches the ransomware’s attempt to infect the system through the use of the DOUBLEPULSAR backdoor before it can execute and thus once again keeps our users protected from this and hundreds of other ransomware families without the need for signatures.
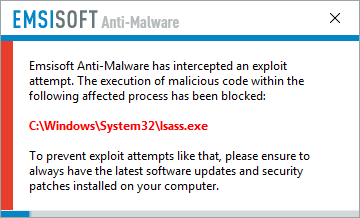
Emsisoft Anti-Malware users are protected from Petya ransomware.
We consider ransomware one of the biggest threats of the past year and plan to do our best to continue our excellent track record in the next year, to keep our users as protected as possible.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free Trial




