Is cryptocurrency mining malware the new adware?

No matter what critics say, it’s clear we’re in the midst of a digital gold rush.
Many cryptocurrencies have exploded in value in recent months; Ethereum, for instance, skyrocketed from $8 at the start of 2017 to $289 at the time of writing, while Litecoin’s value grew from $4 to $50 across the same time period. The total market capitalization of cryptocurrencies jumped to almost $180 bn from $19 bn in only 8 months!
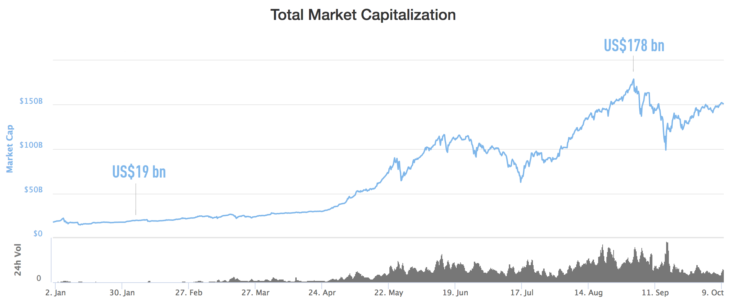
Of course, it’s not only tech-savvy investors who are enjoying the frothy conditions. The lively crypto market has naturally drawn the attention of cybercriminals and hackers, but it’s also attracting crafty website operators who are using sneaky code to turn website visitors into cryptocurrency miners without their consent.
The latter activity raises all sorts of interesting questions. Should in-browser mining be considered criminal activity? Is it simply the next step in the evolution of adware? Or could it be a legitimate way for developers to finance free software?
How does cryptocurrency mining work?
Cryptocurrencies are built on blockchain technology, which is essentially a distributed and decentralized ledger. The term ‘mining’ refers to a user verifying the data in this ledger over and over again. When the blockchain determines enough effort has been put into the verification process, it rewards the miner with a fraction of a digital currency.
Further reading: How cryptocurrency enables ransomware cybercrime
Today, mining is so resource intensive that it’s simply not a profitable undertaking for regular people (with the exception of some minor coins, which are still relatively easy to obtain). However, that hasn’t stopped criminals from coming up with creative ways to hijack the computational power of unsuspecting victims and using their machines to mine for cryptocurrencies. In fact, cryptomining attacks have increased a staggering 600 percent in 2017, according to figures collated by IBM.
Adylkuzz is one of the largest pieces of cryptocurrency mining malware of 2017. Exploiting the same security vulnerabilities as WannaCry, Adylkuzz affected hundreds of thousands of computer earlier this year. After successfully infecting a device, the malware installs itself and uses the victim’s computer’s resources to mine Monero, a cryptocurrency that offers greater anonymity than many of its peers. It could take a single device years to successfully mine cryptocurrency, but when recruited into a large botnet comprised of thousands or millions of devices, the mining is much more profitable (particularly when someone else is paying the electricity bill… you).
It’s only recently that we’ve seen a sharp upswing in the use of cryptomining malware, but it’s important to note that this type of attack has been around for some years. In 2014, tech giant Yahoo accidentally exposed some two million European users to cryptomining malware hidden in ads on the Yahoo homepage. Experts estimated that about 27,000 users were infected per hour the malware was on the site. Meanwhile, in 2015, uTorrent drew heavy criticism for silently bundling bitcoin miner EpicScale in an update.
While traditional cryptomining malware such as these rely on successfully infecting a machine, there’s a new wave of mining malware that requires no interaction beyond visiting a website.
The rise of in-browser cryptocurrency mining malware
All websites have operating costs. The more traffic the website attracts, the greater the costs. Many websites use online advertising to offset these expenses but – surprise, surprise – people don’t like ads. With adblock usage growing by more than 30 percent between 2016 and 2017 and web users becoming more selective with what they click on, it’s harder than ever for websites to sustain themselves using advertising revenue alone.
So what’s the solution?
According to some website owners, the answer lies in cryptocurrency mining. A number of website operators have taken to exploiting their users in order to pay their web hosting bills. Monero is almost always the currency of choice because it is optimized for CPU. JavaScript can manipulate the CPU more effectively than the GPU (graphics adapter), which most other cryptocurrencies are optimized for. By injecting devious JavaScript code known as Coinhive into their sites, website operators are able to harness the processing power of website visitors and use it to mine for Monero.
This all takes place without the visitor’s knowledge or consent because, unlike conventional mining malware, this new breed of cryptojacking doesn’t rely on your engagement. You simply visit the website, and your device is automatically transformed into a miner.
It should come as little surprise that the websites that have been caught using cryptojacking malware are those at the fringes of the internet.
For example, in September users of The Pirate Bay experienced huge system drag when visiting certain pages and soon learned that a Monero JavaScript miner was to blame. Admins of the BitTorrent site quickly responded, framing the in-browser mining as a ‘test’ to see if it could be used to replace the site’s ads, which are often riddled with malware. TorrentFreak estimated the mining malware could be netting The Pirate Bay about $12,000 per month – a figure not to be sneezed at, but a drop in the ocean compared to the $4.4 million ad revenue generated annually by leading torrent sites, as estimated by the Digital Citizens Alliance (PDF).
Showtime, a legitimate video streaming website, was also recently caught using Coinhive. The mining code was quickly pulled off the site but, in contrast to The Pirate Bay admins who were relatively transparent about the miner, Showtime has yet to acknowledge or comment on the situation.
Risks, ethics and legality: A philosophical discussion

In-browser cryptocurrency miners are definitely on the shady side, but are they actually illegal? The answer to this question largely comes down to consent. Many users who’d been duped into mining for The Pirate Bay were upset not because their CPU power was being used to mine Monero, but because they hadn’t been consulted first. Many said they would have gladly opted in if The Pirate Bay admins had been up front from the start and transparent about their intentions.
These sentiments echo what is written in law. In 2015, the New Jersey Division of Consumer Affairs shut down TidBit, software that would allow websites to leverage visitor’s computer resources to mine for Bitcoin. The court ruled that doing so was the equivalent of illegally gaining access to someone’s computer.
“We do not believe Tidbit was created for the purpose of invading privacy,” commented Division of Consumer Affairs Acting Director Steve Lee.
“However, this potentially invasive software raised significant questions about user privacy and the ability to gain access to and potentially damage privately owned computers without the owners’ knowledge and consent.”
It’s Steve Lee’s final word that’s important: consent. In-browser mining without your consent can safely be classed as criminal activity. It devours your CPU power, uses your electricity and potentially leaves you exposed to some privacy and security concerns without giving you the choice of backing out.
If, on the other hand, you consciously agree to allow a website to take control of your hardware in favour of seeing adverts, can it really be considered illegal or malware?
How to prevent your device being hijacked for mining

Regardless of whether you classify in-browser mining as malware, adware or an innovative way to pay the bills, chances are you’ll want to block website operators from taking control of your system’s hardware. Here are a few ways to avoid inadvertently becoming a miner:
- Install No Coin: This lightweight, open-source browser extension monitors sites for potential in-browser mining activity and alerts you if anything suspicious occurs. It also allows you to block and whitelist sites. Available on Chrome, Firefox and Opera.
- Be mindful of CPU spikes: Be conscious of your browsing habits and try to identify any sudden lag or system drag that occurs when you load a website. CPU spikes may also be indicated by computer fans speeding up and making more noise than usual, especially on laptops.
- Avoid piracy sites: Any site may be hiding malware, but it has to be said that piracy sites typically pose a higher risk. Avoid wherever possible.
- Use an antivirus: A reputable antivirus solution can identify potential threats and remove any traditional mining malware that may infect your system.
Looking to the future of cryptomining
While we’re still in the early stages of in-browser cryptocurrency mining, it’s easy to imagine that it may have legitimate applications further down the track. If in-browser mining was standardized (with, say, restrictions on maximum CPU usage and opt in/out policies) it could grow to become an effective alternative to traditional online advertising. In this scenario, in-browser mining could be used as a means of financing free software, or allowing users to support content creators they like – all while removing unsightly, potentially harmful ads from the web.
Alternatively, it could just as easily become the next form of unwanted adware and be a new source of headaches for users across the internet.
Have a glorious (non-consensual mining-free) day!
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialIf you had to choose, would you rather see advertisements or allow websites to use your computer resources to mine cryptocurrencies? Let us know in the comments below!


