Ransomware Profile: DarkSide

DarkSide is a ransomware strain that primarily targets large organizations in the private sector. The group has been highly active since it emerged in August 2020 and has already claimed hundreds of victims, with ransom demands typically falling in the six- and seven-figure range. DarkSide operates with a thin veneer of professionalism and follows corporate-style processes similar to those found in legitimate enterprises.
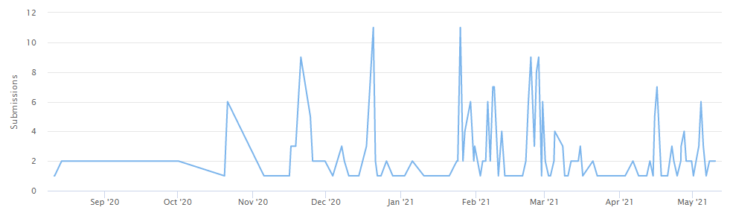
Since DarkSide was first observed, there have been 114 submissions to ID Ransomware, an online tool that helps the victims of ransomware identify which ransomware has encrypted their files (not that not all victims use ID Ransomware, so this number should not be taken to be the total number of successful attacks.) During this time, the group has also published on its leak site the stolen data of more than 80 organizations which presumably refused to pay the demand.
What is DarkSide?
DarkSide is a ransomware variant that encrypts files using SALSA20 and RSA-1024 encryption and demands a ransom typically ranging from $200,000 to $2,000,000 for their decryption. The group claims that their encryption methods are the fastest on the market, with versions of the ransomware available for both Windows and Linux environments. As with many other ransomware groups, DarkSide utilizes double extortion, whereby threat actors not only encrypt the target’s data, but also exfiltrate and threaten to release it if the ransom demand is not paid.
DarkSide operates under the ransomware-as-a-service (Raas) model, whereby affiliates receive a portion of ransom payments in exchange for dropping the malware onto victims’ networks. DarkSide affiliates earn 75 percent to 90 percent of the ransom payments they generate, with the remaining portion going to the DarkSide group.
DarkSide takes many of its operational cues from legitimate businesses. Much like a real company, the group issues press releases, provides real-time chat support, posts software updates and offers deals to attract new affiliates. The group also claims to enforce a code of conduct which prohibits affiliates from targeting certain sectors, performing actions that would cause damage to the reputation of DarkSide, and deploying a competitor’s ransomware in the same campaign.
Like other types of ransomware, DarkSide performs an automatic language check – unusually, using both GetSystemDefaultUILanguage and GetUserDefaultLangID – and will quit without encrypting data if one of the following languages is detected.
- Russian
- Ukrainian
- Belarusian
- Tajik
- Armenian – Armenia
- Azeri (Latin)
- Georgian
- Kazakh
- Kyrgyz (Cyrillic)
- Turkmen
- Uzbek (Latin)
- Tatar
- Romanian – Moldava
- Russian – Moldava
- Azeri (Cyrillic)
- Uzbek (Cyrillic)
- Arabi – Syria
For additional technical details, see Chuong Dong’s analysis.
The history of DarkSide
DarkSide was created by a collective of cybercriminals who claim to have made millions of dollars working as affiliates of other ransomware operations. The group came together to create a new ransomware variant after failing to find the “perfect product” for their needs. DarkSide was extremely active since it was first observed in August 2020, impacting hundreds of organizations across multiple verticals.
In October 2020, DarkSide announced that the group had donated $10,000 in bitcoin to two charities – Children International and The Water Project. In a blog post published on the dark web, the group wrote: “We think it’s fair that some of the money the companies have paid will go to charity. No matter how bad you think our work is, we are pleased to know that we helped change someone’s life.” As it’s illegal to receive funds obtained as a result of a crime, it’s likely that both donations were seized or returned.
DarkSide ransom note
After encrypting the target system, DarkSide drops a customized ransom note titled “README.{userid}.TXT” in all infected directories. The note contains an overview of how much data was stolen, the type of data that was stolen, a link to where the stolen data will be leaked and instructions on how to communicate with DarkSide operators via a TOR browser.
Decryptor performance
According to our performance tests, DarkSide’s decryption tool decrypts files at an average of 231.40MB per second, meaning it would take 72 minutes to decrypt 1 TB of encrypted data. In comparison, our Universal Decryptor tool could recover that data in only 27 minutes.
Our Universal Decryptor can be customized to decrypt almost any type of ransomware, provided that the decryption keys are supplied. The following chart shows the performance of the Emsisoft universal decryptor compared with the decryption tools provided by the Conti, DarkSide, Defray and Ryuk ransomware groups.
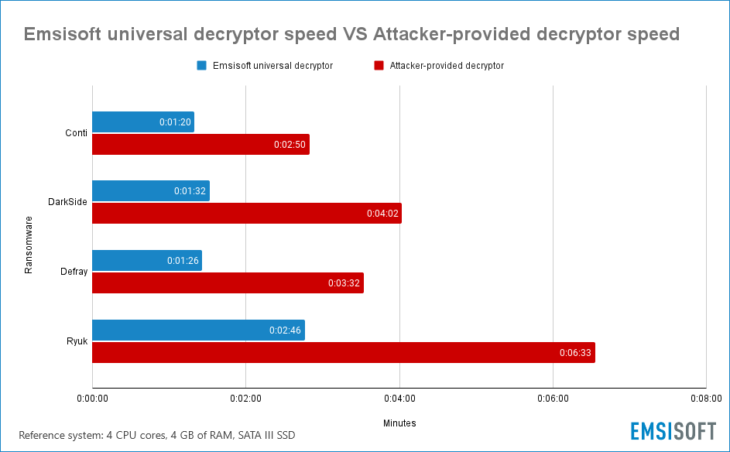
Encrypted dataset: 56 GB collection of 2,234 files ranging from 1 byte to 10 GB in size.
Who does DarkSide target?
Like many other big-game ransomware, DarkSide primarily targets big organizations that have the resources to pay large ransom demands.
However, unlike most other ransomware operations, DarkSide prohibits its affiliates from targeting organizations in the public sector. In fact, according to DarkSide’s code of conduct, there’s quite a long list of prohibited targets, including:
- Hospitals
- Nursing homes
- Palliative care organizations
- Companies that develop and participate in the distribution of the COVID-19 vaccine.
- Morgues
- Funeral homes
- Crematoria
- Schools
- Universities
- Municipalities and state bodies
- Non-profit organizations
How does DarkSide spread?
DarkSide infections typically start with the exploitation of a vulnerable remote service. After the network has been breached, attackers establish command and control via an RDP client routed through TOR, and/or Cobalt Strike. In the reconnaissance stage, attackers use well-known tools such as Mimikatz, advanced_ip_scanner.exe and psexec, among others, to steal credentials and spread laterally until domain admin credentials are obtained.
The ransomware isn’t deployed until the threat actors have mapped out the target environment, exfiltrated data and prepared the system for encryption. The ransomware is delivered in the form of a unique executable customized for the specific organization being attacked. The malware then attempts to delete shadow copies on the target system, terminates processes that could delay encryption and finally begins the encryption process. Encrypted files are appended with a unique extension made using a custom checksum of the victim’s MAC address.
As DarkSide is a RaaS that can be delivered in a multitude of ways, the specific anatomy of an attack can vary from incident to incident.
Major DarkSide attacks
- Companhia Paranaense de Energia: In February 2021, Companhia Paranaense de Energia, a state-controlled electricity company in Brazil, was impacted by DarkSide. During the incident, attackers allegedly stole more than 1,000 GB of company data, including sensitive infrastructure access information, the personal details of management and staff, plaintext passwords and important Active Directory data.
- CompuCom: In March 2021, U.S. managed service provider CompuCom was infected with DarkSide. The attack disrupted a number of services and left some customers unable to access the CompuCom customer portal, but the malware did not spread to customers’ systems. CompuCom estimated that the incident resulted in revenue loss of between $5 million and $8 million, and up to $20 million in recovery-related expenses.
- Colonial Pipeline: In May 2021, Colonial Pipeline, the largest fuel pipeline in the U.S., was hit by DarkSide. The company was forced to shut down some of its IT systems to contain the threat, which resulted in all pipeline operations being temporarily halted and massively disrupted the oil supply chain for much of the eastern U.S. The attack prompted an emergency declaration from the Department of Transportation, which involved lifting regulations on drivers in order to ramp up alternative transportation routes for oil and gas.
How to protect the network from DarkSide and other ransomware
The following practices may help organizations reduce the risk of a DarkSide incident.
- Cybersecurity awareness training: Because the majority of ransomware spreads through user-initiated actions, organizations should implement training initiatives that focus on teaching end users the fundamentals of cybersecurity. Ransomware and propagation methods are constantly evolving, so training must be an ongoing process to ensure end users are across current threats.
- Credential hygiene: Practicing good credential hygiene can help prevent brute force attacks, mitigate the effects of credential theft and reduce the risk of unauthorized network access.
- Multi-factor authentication: MFA provides an extra layer of security that can help prevent unauthorized access to accounts, tools, systems and data repositories. Organizations should consider enabling MFA wherever possible.
- Security patches: Organizations of all sizes should have a robust patch management strategy that ensures security updates on all endpoints, servers, and appliances are applied as soon as possible to minimize the window of opportunity for an attack.
- Backups: Backups are one of the most effective ways of mitigating the effects of a ransomware incident. Many strains of ransomware can spread laterally across the network and encrypt locally stored backups, so organizations should use a mixture of media storage, and store backup copies both on- and off-site. See this guide for more information on creating ransomware-proof backups.
- System hardening: Hardening networks, servers, operating systems and applications is crucial for reducing attack surface and managing potential security vulnerabilities. Disabling unneeded and potentially exploitable services such as PowerShell, RDP, Windows Script Host, Microsoft Office macros, etc. reduces the risk of initial infection, while implementing the principle of least privilege can help prevent lateral movement.
- Block macros: Many ransomware families are delivered via macro-embedded Microsoft Office or PDF documents. Organizations should review their use of macros, consider blocking all macros from the Internet, and only allow vetted and approved macros to execute from trusted locations.
- Email authentication: Organizations can use a variety of email authentication techniques such as Sender Policy Framework, DomainKeys Identified Mail, and Domain-Based Message Authentication, Reporting and Conformance to detect email spoofing and identify suspicious messages.
- Network segregation: Effective network segregation helps contain incidents, prevents the spread of malware and reduces disruption to the wider business.
- Network monitoring: Organizations of all sizes must have systems in place to monitor possible data exfiltration channels and respond immediately to suspicious activity.
- Penetration testing: Penetration testing can be useful for revealing vulnerabilities in IT infrastructure and employees’ susceptibility to ransomware. Results of the test can be used to allocate IT resources and inform future cybersecurity decisions.
- Incident response plan: Organizations should have a comprehensive incident response plan in place that details exactly what to do in the event of infection. A swift response can help prevent malware from spreading, minimize disruption and ensure the incident is remediated as efficiently as possible.
How to remove DarkSide and other ransomware
DarkSide uses sophisticated encryption methods that currently make it impossible to decrypt data without paying for an attacker-supplied decryption tool.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialVictims of DarkSide should be prepared to restore their systems from backups, using processes that should be defined in the organization’s incident response plan. The following actions are recommended:
- Take action to contain the threat.
- Determine the extent of the infection.
- Identify the source of the infection.
- Collect evidence.
- Restore the system from backups.
- Ensure all devices on the network are clean.
- Perform a comprehensive forensic analysis to determine the attack vector, the scope of the incident and the extent of data exfiltration.
- Identify and strengthen vulnerabilities to reduce the risk of a repeat incident.