Fileless malware: Invisible threat or scaremongering hype?

Ransomware may have claimed the lion’s share of media headlines in 2017, but there’s another type of attack that has become increasingly common in recent months – fileless malware.
Deceptive, sneaky and undeniably effective, fileless malware is growing in popularity as cybercriminals trade in brute force for stealth. While some organizations claim traditional antivirus software is all but blind to fileless malware, the truth is that many IT security products are more than up to the challenge.
In addition, there are a few things you can do yourself to minimize the risk of infection and limit the fallout should something happen to slip past your defenses. Read on to find out how you can protect yourself from the ‘invisible’ threat that is fileless malware.
What is fileless malware?
Fileless malware goes by many names, including ‘non-malware’, ‘memory-based malware’ and ‘living off the land attacks’. Whatever you choose to call it, fileless malware refers to a special type of cyberattack that can infect a system with malware without leaving an executable file on disk. It’s not fileless in the sense that no files are involved whatsoever; rather, the term refers to the fact that – unlike conventional malware – fileless malware can deliver its payload without dropping anything suspicious onto a machine’s hard drive.
So, if fileless malware isn’t stored on your hard drive, where does it live?
1. In your RAM
Random access memory (RAM) is a form of computer data storage that allows information to be stored and retrieved temporarily. Some strains of fileless malware can reside in your RAM and remain there until executed without stepping foot on your hard drive. This type of fileless malware is relatively rare because it can only survive until you restart your computer, which completely clears the RAM.
While this might seem like a futuristic concept, it’s worth noting that memory-resident malware has been around in one form or another for decades. For example, back in 2001, the Code Red worm spread like wildfire, infecting almost 360,000 computers by exploiting a vulnerability in Microsoft IIS web servers – all without leaving the RAM of the infected system.
2. In the Windows Registry
With the shortcomings of RAM-based malware in mind, cybercriminals have developed a new type of fileless malware that resides in the Windows Registry. The Windows Registry is an enormous database that stores low-level settings for the Windows operating system as well as all the applications that use the registry. Kovter and Poweliks are two examples of fileless malware that make use of the Windows Registry to infect users without leaving any incriminating files on disk.
In most cases, the malware relies on the use of native Windows tools such as PowerShell and Windows Management Instrumentation (WMI).
How does fileless malware end up on your machine? While the infection process can vary between malware families, it often looks something like this:
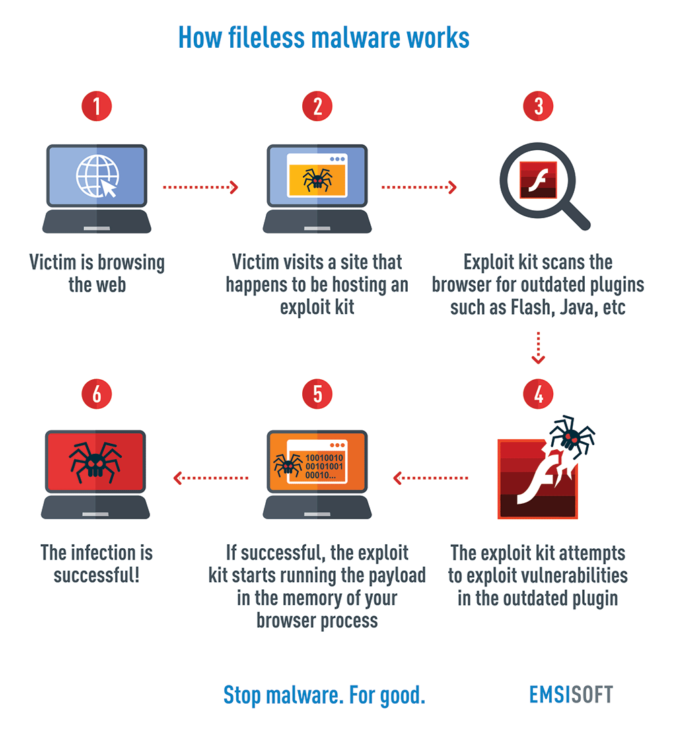
- You’re browsing the web
- You visit a site that happens to be hosting an exploit kit
- The exploit kit scans your browser for outdated plugins such as Flash, Adobe, Java or Microsoft Silverlight
- The exploit kit attempts to exploit vulnerabilities in the outdated plugin
- If successful, the exploit kit starts running the payload in the memory of your browser process.
- The infection is successful!
Why are fileless malware attacks becoming more common?
Fileless malware is on the rise. In fact, some reports estimate that as many as 4 in 10 businesses in the US were compromised by fileless malware in 2017.
What’s responsible for this trend?
It’s the path of least resistance. As noted, fileless malware does not reside on a computer’s hard disk. Some antivirus products rely solely on checking file attributes to determine whether a file is safe or potentially malicious and do not take into account the behavioral patterns of the attack. Fileless malware has less chance of being detected than conventional malware, which means the criminals have a higher chance of success, whether that’s encrypting your files, stealing your passwords or something similarly destructive.
Our users can rest assured that Emsisoft Anti-Malware makes use of advanced behavioral identification methods to recognize and stop both regular and fileless malware. However, not all antivirus products are so thorough and, given that there are no suspicious files to actually check, many fileless malware fly under the radar. There is simply less chance of being detected.
Another factor to blame for the increase in fileless malware attacks is the growing popularity of exploits as a service, a relatively new phenomenon in which criminals deploy cyberattacks on behalf of the buyer. This illegal service means that even the least tech-savvy criminals have the means to unleash a devastating fileless malware attack on the target of their choosing.
Fileless malware protection 101
There’s no denying that fileless malware are sneaky critters, but the good news is that there are a number of things you can do as a user to minimize the risk of infection. Protect yourself against fileless malware by:
1. Keeping your apps and operating system up to date
One of the most effective ways to keep your system safe from malware is to simply keep all your software up to date with the latest security patches. As many as 85 percent of all targeted attacks can be prevented by simply applying the latest software patches, according to figures from the U.S. government. For the ultimate peace of mind, ensure auto updates are enabled in the settings of your applications.
2. Disable PowerShell
Windows PowerShell is a native Microsoft tool used for task automation and configuration management. Unfortunately, fileless malware often exploits certain vulnerabilities in PowerShell. If you don’t need to use PowerShell (and most home users probably don’t), use the following steps to disable it:
Windows 10:
- Press the Windows key
- Type “Control Panel”
- Open Control Panel
- Click Programs
- Click Turn Windows features on or off
- Scroll down to Windows PowerShell and untick
- Click OK
3. Monitor traffic logs for suspicious traffic
Both fileless and conventional malware leave clues as to their existence, most commonly in the form of affecting your network’s traffic. If you notice network activity that is substantially different from the status quo, it’s possible that you may have been infected.
There are many tools you can use to do this, including the native Windows Firewall. Check out this How-To Geek article for step by step instructions on using Windows Firewall logs to track network traffic and identify suspicious behavior.
4. Use an antivirus with behavioral detection
As we mentioned earlier, detecting fileless malware can be a challenging task for some antivirus products that focus exclusively on file properties. With this in mind, it’s important to choose antivirus software that can analyze your system’s behavior and pinpoint suspicious activity. By recognizing changes to the system’s usual patterns of behavior, these security solutions can identify malicious activity and promptly block and remove the threat.
5. Adopt the principle of least privilege
A cornerstone of IT security, ensure that every user on the system has the lowest clearance needed to perform their task. This helps keep the damage to a minimum should a piece of fileless malware happen to slip past your computer’s defenses.
Is my current antivirus enough to protect against fileless malware?
The notion that fileless malware is completely invisible to conventional antivirus products is little more than marketing hype. Although it doesn’t reside on the hard drive, many modern IT security solutions have evolved past the point of simple file scanning and are more than capable of revealing and removing zero-day malware threats, regardless of where they choose to hide.
Fileless malware attacks could very well become even more common in the months and years ahead. But despite the sinister name and scaremongering from some organizations, the fact remains that reputable antivirus products such as Emsisoft Anti-Malware will be up to the challenge of keeping your computer safe from harm.
What’s your strategy for dealing with fileless malware? Let us know in the comments!
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialHave a terrific (malware-free) day!


