Spotlight on ransomware: Ransomware encryption methods
The WannaCry ransomware outbreak has raised many questions about how ransomware works and what can be done about it. How does it get into a system? What does it do when it’s in there? Our Spotlight on Ransomware series explores the different stages of a ransomware attack. This week’s focus: ransomware encryption.
A ransomware infection is one of the fastest ways to have all of your personal files encrypted and potentially lost forever. Employing encryption makes the criminal’s threat credible and gives malware authors control over your data. With encryption methods employed getting more and more sophisticated, it is becoming harder for the good guys to provide free help.
Follow us as we explain what file encryption is, the different methods ransomware developers use and why understanding encryption is crucial to recovering victims’ files.
Before we dive in, if you aren’t familiar with how ransomware gets into a system or what it does once it’s in there, start here.
A brief background on cryptography and cryptanalysis
Cryptography (from greek: hidden or secret writing) is the practice of techniques that prevent third parties or the public from reading private messages. It uses encryption to scramble plaintext (the unencrypted data) into ciphertext (the encrypted data) to obfuscate the content of the message to third parties looking in.
There are 4 main objectives to cryptography:
- Confidentiality: only the intended recipient can understand the message,
- Integrity: the message cannot be edited without the tampering being detected,
- Non-repudiation: the sender cannot deny their intentions in creating the message, and
- Authentication: the sender and recipient can identify that they are communicating with one another.
Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, and electrical engineering, and has broad applications including military communications, electronic commerce, ATM cards, computer passwords. Basically anything where secure communication is essential.
Cryptanalysis, defined as the study of cryptographic systems with the goal to find weaknesses and retrieve the contents of encrypted messages, evolved in parallel with cryptography. Even though the word was only coined in the 1920s, the practice of breaking codes and ciphers dates back as far as the 9th century. Cryptanalysis played a decisive part during World War II to decipher German intelligence secured by Enigma machines, which used an unencrypted symmetric key for both the sender and receiver of the message.
Since then, the emergence and explosive growth of computing power allowed ever more complex encryption methods that are not only used to secure your email messages and web traffic but also, sadly, to hold your files for ransom by cyber criminals.
Encryption methods: Symmetric v asymmetric
Encryption methods have become incredibly complex compared to the earliest substitution ciphers used by Julius Caesar, where the plaintext letters are simply replaced by shifting it back or forth a fixed amount of positions along the alphabet.
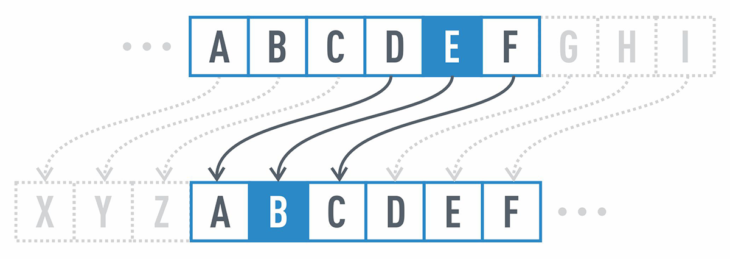
Since the structure of the plaintext is the same as the encrypted message, it’s easy to spot patterns using frequency analysis to identify how often and in which sequence the characters appear.
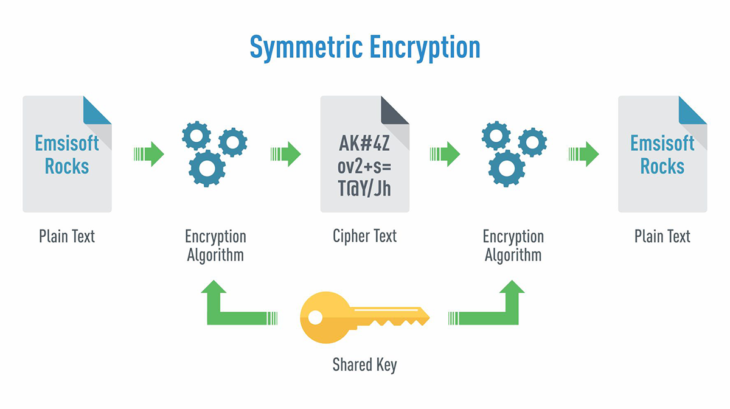
Symmetric encryption: Fast but vulnerable
Yet the above cipher is a simple example of how symmetric encryption works: both the sender and the receiver shift the letter the same fixed number of positions. This number of positions is what is referred to as the “key”. It is therefore imperative that the key is kept secret, which is why symmetric encryption is often referred to as “secret key encryption”.
There are two major types of symmetric encryption: Block ciphers and stream ciphers.
As the name implies, block ciphers operate by encrypting in byte-sized blocks using the same key. The message itself is split across multiple blocks depending on the length, and predictable data is appended to extend it to a full block in a process known in cryptography as padding. The most common block ciphers you’ll come across are AES and Blowfish, the former of which is often used in ransomware encryption (more on that further down in the article).
Stream ciphers, on the other hand, encrypt each digit of the plaintext at a time (usually in the form of a bit), with the help of a pseudo-random key stream. This means a different key from the stream is used for each of the bits. A mathematical operator “exclusive or” (XOR, for short) then combines the the two to create the ciphertext. Common stream ciphers in use today include RC4 and Salsa20.
What characterizes each of these symmetric encryption methods is that they have low computational requirements to function, and use only one key for both encryption and decryption of the message.
The latter raises an important question however: how do you secretly communicate the key without someone listening in on the exchange?
Asymmetric encryption: Secure but slow
Asymmetric encryption, also known as public key encryption, has the answer: it uses a pair of keys, consisting of a public and a private one.
The public key is intended to be distributed widely, while the private key is only in the possession of the key pair owner. Messages encrypted with the public key can only be decrypted using the private key, while messages encrypted with the private key can only be decrypted using the public key.

As a result, asymmetric encryption algorithms not only allow you to encrypt and decrypt messages, but also allow for authentication of that message, as only the private key owner can create a message decryptable by the public key.
At the base of most asymmetric cryptography systems is usually an algorithm that requires computationally heavy operations. The most common in use today are Diffie-Hellman-Merkle, RSA and Elliptic Curve Cryptography. While explaining each of these would be beyond the scope of this article, there’s a fairly in-depth article on ArsTechnica if you’re brave enough to dive into the maths behind them.
The bottom line is that asymmetric encryption allows for relatively secure encryption without the need of a shared secret key, yet the complex computational nature makes it unfeasible for large sets of data.
Given that both encryption types have their unique advantages and disadvantages, most implementations (including ransomware authors) will use a combination of both: symmetric encryption with a randomly generated key, usually referred to as the session key, to encrypt the actual message or files, then an asymmetric algorithm to encrypt the session key used.
Common cryptology terms
Message: The data that you want to protect through encryption; this can be text as in an actual message or a file
Plaintext: The unencrypted message
Ciphertext: The encrypted message
Key: The component that is used by an encryption algorithm to turn a plain text into a ciphertext and vice versa.
Block cipher: symmetric encryption in blocks of bytes.
Stream cipher: use of a keystream to encrypt one bit at a time.
Symmetric (secret) key encryption: The same key is being used for encryption and decryption of a message.
Asymmetric (public) key encryption: Different keys are being used for encryption and decryption of a message.
How ransomware authors use encryption: CryptoLocker
To see how exactly malware authors use encryption for their nefarious purposes we are going to take a look at the one ransomware family that was so prolific and widespread that its name is, to this day, used synonymously for all ransomware: CryptoLocker.
CryptoLocker was certainly not the first file encrypting ransomware, but it definitely was the first major ransomware family that got widespread media attention. It uses 256 bit AES symmetric encryption for the actual file encryption, and asymmetric RSA encryption for communication and securing the symmetric session key.
Unsurprisingly, the way CryptoLocker operates has become a blueprint for many other ransomware families that followed, making it an ideal case study to show how it uses encryption to lock up your files.
- Establishing secure communications
When it arrives on a system, CryptoLocker comes with nothing more than a RSA (=asymmetric) public key, used by the ransomware to establish a secure channel to its command and control server. The ransomware handles all communication between itself and the malware author’s server via this channel. Using public key encryption has two major advantages in this case:
- Any third parties listening in on the network communication won’t be able to see the plaintext messages being exchanged between CryptoLocker and its server. All a malware analyst would see when trying to understand the protocol by sniffing the network traffic is a bunch of encrypted gibberish.
- More important however is that malware authors not only hide their messages from prying eyes, but also ensure that the server the ransomware is talking to belongs to the malware authors.
Remember: Any public key only decrypts messages that were encrypted by their corresponding private key, which only the malware author will have access to.
As a result, encrypting the communication with RSA not only ensures its secrecy but also its authenticity. This way, a law enforcement agency seizing command and control domains can’t simply take over control of the malware by issuing its own commands.
- Encrypting the files
During the communication, CryptoLocker will request a second RSA public key from its server that is unique to the victim. It then goes ahead and creates a 256 bit AES session key that it will use to encrypt the victim’s files. As mentioned before, asymmetric cryptography like RSA isn’t well suited to encrypt large amounts of data directly as it is relatively slow compared to its symmetric cousins. Using a symmetric algorithm like AES to encrypt the bulk of the user data is therefore much more efficient.
- Securing the shared key
As a final step, CryptoLocker encrypts the 256 bit AES key using the victim-specific, asymmetric RSA public key and stores it together with the encrypted file data.
Once the encryption process finishes, the ransomware will erase the AES session key from its memory, making sure no trace is left anywhere. Only the owner of the victim’s private key, which was generated and is stored only on the malware author’s server, is able to decrypt the AES session key from within the encrypted files and decrypt the files again once the victims have paid the ransom.
Ransomware leverages the advantages of both asymmetric and symmetric encryption to lock up the victim’s files within a matter of seconds, rather than hours. Recovering them without paying the criminals is almost impossible.
Almost…
Understanding encryption helps fight ransomware
Analyzing ransomware encryption is incredibly complex. We barely scratched the surface in this article, yet this high level overview of how ransomware locks up your files will give you an idea of the hard work our Lab team does on a daily basis to try and create ransomware decrypters to help affected victims. For free!
Sometimes we are lucky: Ransomware that solely relies on symmetric encryption, such as Harasom, “hides” the same key it uses to encrypt every file on every system in the ransomware executable itself.
We wish ransomware authors always made it this easy…
Cryptolocker’s more complex encryption makes it much harder to crack, yet it also opens the door for flaws in the implementation, just as bugs sneak into legit, professional applications that make them exploitable.
Take CryptoDefense for example: this ransomware family launched after CryptoLocker and used almost exactly the same approach with one minor difference: Instead of the server generating the private and public key for the victim, it generated the key pair on the victim’s system and then sent it off to its command and control server. Fortunately for us, the CryptoDefense authors didn’t read the documentation of the encryption library they used properly and accidentally saved the generated key pair on the victim’s system. From there it was easy for us to find those keys and use them to restore any of the victim’s files.
Protection is better than cleaning up the mess
As with all types of malware, it’s better to be protected in the first place then trying to clean up afterwards. This is even more relevant in the case of ransomware. So don’t wait until it’s too late and make sure you’re protected by a reputable anti-malware solution.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialHave a nice, ransomware-free day!